- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- What’s New in 2012 R2: Making Device Users Productive and Protecting Corporate Information
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

Part 2 of a 9-part series .
The modern workforce isn’t just better connected and more mobile than ever before, it’s also more discerning (and demanding) about the hardware and software used on the job. While company leaders around the world are celebrating the increased productivity and accessibility of their workforce, the exponential increase in devices and platforms that the workforce wants to use can stretch a company’s infrastructure (and IT department!) to its limit.
If your IT team is grappling with the impact and sheer magnitude of this trend, let me reiterate a fact I’ve noted several times before on this blog: The “Bring Your Own Device” (BYOD) trend is here to stay .
Building products that address this need is a major facet of the first design pillar I noted last week : People-centric IT (PCIT).
In today’s post (and in each one that follows in this series), this overview of the architecture and critical components of the PCIT pillar will be followed by a “ Next Steps ” section at the bottom. The “Next Steps” will include a list of new posts (each one written specifically for that day’s topic) developed by our Windows Server & System Center engineers. Every week, these engineering blogs will provide deep technical detail on the various components discussed in this main post. Today, these blogs will systematically examine and discuss the technology used to power our PCIT solution.
Our goal is to walk you through the architecture, examples and critical components to each pillar. The “Next Steps” section provides an easy way to review all of the supporting analysis from our engineering teams about the inner workings of the technology at work within Windows Server & System Center.
Getting in depth on PCIT is a major topic of countless discussions I’ve had with business leaders all over the world. In each of these meetings my feedback has been pretty straightforward: The number and diversity of devices in your company is only going to increase; this is a trend you really want to embrace.
This doesn’t mean that there aren’t organizations doing their best to fight back the tide, but I do believe that the companies who embrace the opportunity to keep their employees connected and productive will see a justifiable return on their investment (ROI).
Making that ROI materialize, however, will depend on how an organization embraces and enables the BYOD trend. In particular, every IT team will need to carefully and individually identify the right balance of access to corporate resources from these devices and then ensure that the necessary security and compliance protocols are enforced. Getting this right can have a big impact on employee morale, and a hassle-free IT environment can even impact retention.
We have made a big investment in PCIT because we want to enable and empower IT pros to provide their workforce with strong and stable support for the devices they want to work from, while also providing these IT teams with the means to take the appropriate amount of control of those devices – both corporate-supplied and user-owned. The PCIT solution detailed below enables IT Professionals to set access policies to corporate applications and data based on three incredibly important criteria:
- The identity of the user
- The user’s specific device
- The network the user is working from
The solutions we’ll detail in these PCIT posts enable IT teams to tightly control devices based on the type of work they do and the sensitivity of the corporate data they access. For example, very strict security protocols, usage controls, and data access requirements are necessary for point-of-sale devices, devices on a manufacturing line, devices in a heavily regulated pharmaceutical lab, bank-teller PCs, etc. The need for these kinds of devices to be connected and managed will continue to be critically important. On the other end of the spectrum you have devices such as personal phones and tablets that IT simply cannot control in the same way (Here is a test: Try telling your end-users that you’re going to disable the cameras on their personal phones and see what their reaction is!).
What’s required here is a single management solution that enables specific features where control is necessary and appropriate, and that also provides what I call “governance,” or light control when less administration is necessary. This means a single pane of glass for managing PCs and devices. Far too often I meet with companies that have two separate solutions running side-by-side – one for every PC, and the second to manage devices. Not only is this more expensive and more complex, it creates two disjointed experiences for end users and a big headache for the IT pros responsible for managing.
In today’s post, Paul Mayfield , the Partner Program Manager for the System Center Configuration Manager/Windows Intune team, discusses how everything that Microsoft has built with this solution is focused on creating the capability for IT teams to use the same System Center Configuration Manager that they already have in place managing their PCs and now extend this management power to devices. This means double the management capabilities from within the same familiar console. This philosophy can be extended even further by using Windows Intune to manage devices where they live – i.e. cloud-based management for cloud-based devices. Cloud-based management is especially important for user-owned devices that need regular updates.
This is an incredible solution, and the benefit and ease of use for you, the consumer, is monumental.
* * *
As you may have seen at the recent TechEd events, we have added several new capabilities across Windows, Windows Server, System Center and Windows Intune this year. These new capabilities are intended to enable our customers to embrace the Consumerization of IT and enable a Bring Your Own Device (BYOD) scenario in their organizations around the world.
We refer to these new capabilities as “ People-centric IT .”
People-centric IT (PCIT) is about helping people to work on the devices they choose. We’re providing users access to their apps and data on any of their devices in any location. The challenge this presents to IT teams is considerable: As soon as users are working on a device that IT does not manage (or even have any knowledge of), it becomes very difficult to retain control of sensitive corporate information and to be able to respond to situations such as the device being sold, lost, or stolen.
In particular, the challenges faced by IT teams responsible for a modern corporate infrastructure come from four key areas:
With the 2012 R2 wave of releases (e.g. Windows Server, System Center Configuration Manager, and the next release of Windows Intune), we are helping our customers answer these challenges. Engineers across each of those teams have jointly planned and executed their scenarios across a common set of engineering milestones, and we have delivered these scenarios across three primary areas that drove our priorities and investments in engineering:
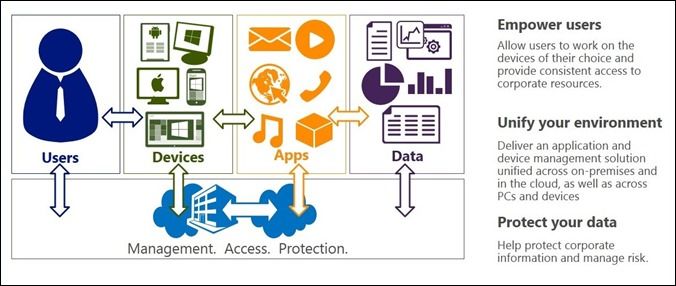
- Empowering users . This means allowing users to work on the devices of their choice by providing consistent access to corporate apps and data from those devices. We’ll support a broad set of devices in the R2 wave of releases this year, ranging from corporate laptops and desktops to personal phones, laptops, and tablets. We’ll support Windows and iOS devices across all of our PCIT features. Many features will be supported on Android too. For example, enrolling devices for management will be supported across Windows, iOS and Android. WorkPlace Join and Work Folders will be initially supported on Windows and iOS.
- Unifying your environment . With the System Center Configuration Manager console we deliver comprehensive application and device management from a single plane of glass. We’ve also worked to integrate scenarios across on-premises infrastructure (using System Center Configuration Manager, Windows Server, and Active Directory), as well as cloud-based services, (using Windows Intune and Windows Azure). Also, it’s worth noting that, on top of all this, we have already integrated management and malware protection.
- Helping protect your data . By controlling access to information based on a user, his/her specific device, and the location of that device, IT teams can better control and safeguard corporate assets. These tools can also remove or disable data on devices when they are no longer being used, as well as provide rich auditing and reporting.
Now let’s look at each of these scenarios, and their benefits, in detail.
Empower users
Simple registration and enrollment for users adopting Bring Your Own Device (BYOD) programs
We’re providing new ways for users to opt-into receiving IT services on their devices. Users can perform a Workplace Join to register their devices in Active Directory and they can enroll their devices for management in Configuration Manager and Windows Intune.
You can think of Workplace Join as being a light form of Domain Join but for personal mobile devices. Registered devices are recorded in the Active Directory and they are issued credentials. However, they don’t support Group Policy or scripting. Instead, you can manage the device by enrolling it for mobile device management.
We’re making it simple and easy for users to register their device with the Active Directory. They will want to register their devices in order to get access to corporate resources and in order to enable single-sign-on (SSO).
Based on the user’s name and password, we’ll look up the tenant (in the case of Azure Active Directory) or look up the local Active Directory Federation Services (AD FS) registration server (in the case of on-prem registration). Then we trigger the device to enroll for a certificate from its registration service.
As part of that Workplace Join, we’ve created a user@device record in the Active Directory. In this way, we’re enabling your existing AD infrastructure to be extended to accommodate mobile devices. This allows us to provide the IT Pro with an inventory of devices and their users, and to audit the access that will be subsequently granted to those users on those devices. The certificate issued to the device includes both the identity of that device and the identity of the authenticated user. Access to resources published via our Web Application Proxy (see below), or to any other resource that relies on AD FS for authentication, will rely on this certificate for authentication.
One thing worth noting: The act of registering the device to Active Directory does not allow IT to control the device in any manner -- that’s is covered by enrollment. Workplace Join is only used to govern access to corporate resources and to enable SSO.
In addition to registering devices with Active Directory, we’re also making it easy for users to enroll their devices into the Windows Intune management service. Users will want to do this in order to get their devices provisioned, and in order to install corporate apps on their devices. To do this, the user simply enters his or her user name and password to enroll the device, and the service will then look up the user’s tenant and trigger Mobile Device Management (MDM) enrollment.
MDM enrollment varies by device. The basics of MDM enrollment include issuing a certificate to authenticate the device to the management system, installing management profiles, and registering a device with an appropriate notification service. As part of the enrollment process, the user will be prompted to consent to allow some administrative control of the device to the IT department. Once enrollment is complete, the management system triggers device provisioning. The device will contact the Windows Intune service and download settings, WiFi Profiles, VPN profiles, side loading keys, apps and more. The device may also enroll for additional certificates that can be used for network authentication or for other security purposes.
A user can decide to register the device with Active Directory or enroll the device in Windows Intune – or both. We recommend both because the full suite of PCIT services and experiences are only available to devices that are both registered and enrolled. This is the best experience for the user and it provides the best protection for the company.
Access to company resources consistently across devices
The company portal (see sample screenshot below) provides users with a consistent interface from which they can gain access to applications (both internal applications and links to public stores), manage their own devices to perform tasks such as remote wipe, and also gain access to their data with integration to Work Folders.
Automatically connect to internal resources when needed
As part of enrolling for management, users can have their devices provisioned with certificates, WiFi profiles, VPN profiles, and DirectAccess configuration. The VPN profiles can be associated with DNS names or specific applications so that they automatically launch on demand. This allows users to work remotely and always be connected to the corporate network without the need to initiate a VPN connection.
A new feature (shown below) with Windows Server 2012 R2, System Center 2012 R2 Configuration Manager, and Windows 8.1 is the ability to configure applications to initiate the VPN connection when the application is launched.
Users can work from the device of their choice to access corporate resources regardless of location
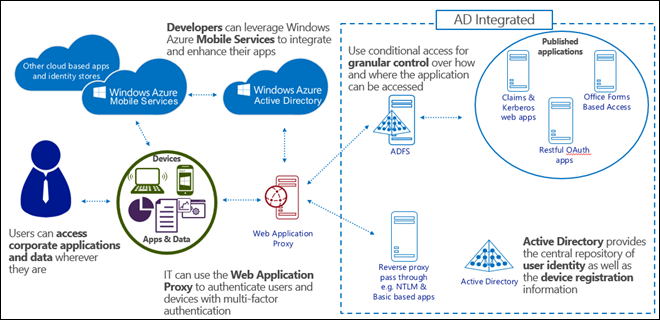
New in Windows Server 2012 R2 are the Web Application Proxy and Work Folders . The Web Application Proxy provides the ability to publish access to internal resources and to optionally require Multi-Factor Authentication at the edge.
Here’s an example of how it might work:
- After the user registers her device and enrolls it for management, she is given access to the Company Portal app.
- From the Company Portal, she installs (side-loads, in this example) a line of business app.
- When she launches the app, the app contacts the Web Application Proxy to get access to the backend web service it needs.
- The Web Application Proxy redirects the app to authenticate with AD FS.
- AD FS has been configured to challenge the device for the certificate acquired via device registration (Workplace Join).
- AD FS verifies that the user is authorized to access this corporate resource from this specific device. However, in this example, AD FS has been configured to also challenge the user for an additional factor of authentication when a device is connecting from the Internet.
- AD FS calls into the multi-factor authentication (MFA) plug-in (supports integration with any 3rd party MFA provider). For example, the MFA plug-in may challenge the user to enter a code on their phone.
- Once the multi-factor authentication requirement is satisfied, AD FS completes the authentication.
- The Web Application Proxy then permits the app to access its backend service.
Work Folders is a new file sync solution that allows users to sync their files from a corporate file server to their devices. The protocol for this sync is HTTPS based. This makes it easy to publish via the Web Application Proxy. This means that users can now sync from both the Intranet and the Internet. It also means the same AD FS-based authentication and authorization controls described above can be applied to syncing corporate files. The files are then stored in an encrypted location on the device. These files can then be selectively removed when the device is un-enrolled for management.
Unify your environment
On-premises and cloud-based management of devices within a single console
One important data point for us when we planned People-centric IT was the feedback we gathered from customers about the need to help reduce client management infrastructure costs and complexity. To do this, we worked hard to integrate Configuration Manager and Windows Intune. Our vision was for IT teams to use the Configuration Manager Administrator console to “manage devices where they live,” on-premise desktops and laptops can be serviced through existing on-prem infrastructure, and Internet-connected devices can be serviced through cloud infrastructure.
All of this functionality is now available – the management of all of these devices and all of this infrastructure can be in one place with the Configuration Manager console which is already very widely used. Client management and security are now offered in a unified single solution which makes it easier to manage devices and applications, and to address threats and non-compliance. If you’re a current Configuration Manager customer, adding the Windows Intune cloud-based management is quick and easy: Just deploy an Intune connector to your existing System Center 2012 Configuration Manager deployment and you’re ready to go.
Simplified, user-centric application management across devices
With Configuration Manager and Windows Intune, we’ve made it easy to ensure that applications are delivered in the optimal method for each device to ensure worker productivity. Configuration Manager allows the administrator to define the application once and then target it to a user or group. It evaluates the user’s device type and network connection capabilities, and then delivers the appropriate method (local installation, App-V, RemoteApp, etc). As a result, whether your employee is using a laptop, VDI session, or iPad – or all of these – you can deliver the app to that user with the best experience on each device.
Because of the integration between Windows Intune and Configuration Manager, you can also extend application delivery to all major device types while still centrally managing application delivery across devices from a single console (see graphic below). Applications can include locally-installed MSI packages or App-V applications on Windows devices, remote applications using Microsoft virtualization solutions, web links, or public applications stored in the Windows Store, App Store, or Google Play.
Comprehensive settings management across platforms, including certificates, VPNs, and wireless network profiles
We’ve substantially expanded our settings management capabilities across platforms, including certificates, VPNs, and wireless network profiles. Policies can be applied across various devices and operating systems to meet compliance requirements, to the extent of the capabilities exposed on those platforms and we have extended native management for Windows RT, iOS and Android. IT teams can provision certificates or VPN and Wi-Fi profiles on mobile devices, and get a full app inventory and application push install for corporate-owned devices. There is also functionality to look into the inventory of “managed” apps and publishing of apps for personal devices, and IT teams can remotely wipe and unregister devices from management system (as supported by each operating system).
IT can better protect corporate information and mitigate risk by being able to manage a single identity for each user across both on-premises and cloud-based applications
As users blend their work and personal lives, and as organizations adopt a mixture of traditional on-premises and cloud-based solutions, IT teams need a way to consistently manage the user’s identity and provide users with a single sign-on to all their resources. We’re helping IT departments do this by providing users with a common identity across on-premises or cloud-based services leveraging existing Windows Server Active Directory investments, and then connecting to Windows Azure Active Directory .
A common part of connecting on-prem AD to Azure AD is deploying Active Directory Federation Services . Windows Server 2012 R2, we have significantly enhanced AD FS to be easier to deploy and configure, and we’ve tightly integrated it with the Web Application Proxy for simple app publishing (see graphic below).
Help protect data
IT can access managed mobile devices to remove corporate data and applications in the event that the device is lost, stolen, or retired from use
Whether a device is lost, stolen or simply being repurposed, there will be times when IT needs to ensure that the corporate information stored on the device is no longer accessible. With the R2 wave of releases, we have added the ability to selectively wipe corporate information while leaving personal data intact.
|
Content removed when retiring a device |
Windows 8.1 Preview |
Windows 8 RT |
Windows Phone 8 |
iOS |
Android |
|
Company apps and associated data installed by using Configuration Manager and Windows Intune |
Uninstalled and sideloading keys are removed. In addition any apps using Windows Selective Wipe will have the encryption key revoked and data will no longer be accessible. |
Sideloading keys removed but remain installed. |
Uninstalled and data removed. |
Uninstalled and data removed. |
Apps and data remain installed. |
|
VPN and Wi-Fi profiles |
Removed. |
Not applicable. |
Not applicable. |
Removed. |
VPN: Not applicable. Wi-Fi: Not removed. |
|
Certificates |
Removed and revoked. |
Not applicable. |
Not applicable. |
Removed and revoked. |
Revoked. |
|
Settings |
Requirements removed. |
Requirements removed. |
Requirements removed. |
Requirements removed. |
Requirements removed. |
|
Management Client |
Not applicable. Management agent is built-in. |
Not applicable. Management agent is built-in. |
Not applicable. Management agent is built-in. |
Management profile is removed. |
Device Administrator privilege is revoked. |
IT can set policy-based access control for compliance and data protection .
With users working on personal devices, there are real challenges to ensure compliance standards are met and that information is protected. Inside Windows Server 2012 R2, we’ve added new capabilities in the Web Application Proxy, AD FS, and Work Folders to make it easy for IT teams to make resources available but also remain in control of data.
With the Multi-Factor Access Control capability in AD FS, access control policies can be authored using multiple criteria, including the identity of the user, the identity of the device, whether the request is coming from intranet or extranet, and any additional authentication factors used to identify the user.
As we showed at the TechEd Europe keynote in Madrid, Work Folders is integrated with Dynamic Access Control , providing the ability to automatically classify information based on content, and perform tasks such as protecting with Rights Management Services – even for data that is created and stored on clients!
Bringing it all together!
To see People-centric IT, including System Center 2012 R2 Configuration Manager, Windows Intune, and Windows Server 2012 R2 in action, you can watch a complete presentation and end-to-end demonstration from the TechEd North America Foundational Session here . You can also learn more about People-centric IT by downloading the People-centric IT Preview Guide .
Be sure to download System Center 2012 R2 Preview Configuration Manager and Windows Server 2012 R2 Preview today!
* * *
Over the last 20 years I have led a number of PC/Device management teams, and I have seen every possible variety of software solution along the way. I truly believe that what we are delivering in this 2012 R2 wave is the single most complete and comprehensive solution that has ever been released for enabling users across PC and devices. It’s amazing to see what our early foundations have helped us build for our users today.
These 2012 R2 products deliver a unified solution to end-users across PCs and devices, and, when you consider the need for this product to be powerful and scalable for the IT teams using it – there is simply no better platform for IT pros.
I encourage everyone to spend a few minutes today creating an account on Windows Intune (you can use the entire solution – with no capabilities held back – for a free 90 day trial) and test drive the management power available in this remarkable product. Try enrolling a few PCs and devices to the service* and start experimenting with managing your devices from the cloud – I think you’ll be impressed.
- Brad
NEXT STEPS:
To learn even more about the technical topics discussed today, check out these posts from our engineering teams:
-
Compliance Settings and Company Resource Access in Configuration Manager
This post outlines how System Center Configuration Manager and Windows Intune allows an administrator to provide VPN, WiFi profiles, and Certificates to permit users to connect to company resources. -
Protecting Corporate Data on Mobile Devices by using Configuration Manager and Windows ...
This is an overview of how System Center Configuration Manager and Windows Intune provide the ability for the administrator or user to protect corporate data on mobile devices by leveraging retire and wipe functionality. -
User experience with Unified Device Management using System Center 2012 R2 Configuratio...
This post examines how System Center Configuration Manager and Windows Intune provide the user with a consistent enrollment and resource access experience across devices. -
Simplified, User-centric Application Management across Devices with System Center 2012 ...
In this post, the team looks at how System Center Configuration Manager and Windows Intune allow administrators to extend application delivery to all major device types while still centrally managing application delivery across devices from a single console. -
Extending device support in Active Directory
An analysis of Active Directory in Windows Server 2012 R2 and its capabilities to enable People Centric IT -
Enabling Modern Work Styles using Windows Server 2012 R2 Remote Desktop Services
...
An overview of the improvements made to Microsoft VDI (Remote Desktop Services) reducing storage related costs, improving the end user experience, and administration improvements to both session and VM based VDI. -
Introducing Work Folders on Windows Server 2012 R2
Work Folders enables IT administrators to provide Information Workers the ability to sync their work data on all their devices wherever they are while remaining in compliance with company policies. This is done by syncing user data from devices to on-premise file servers.
* In the current production service you will not see the complete set of device management capabilities enabled yet – we are running an invitation-only customer preview on a pre-production service. You will see these capabilities later this year.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.