Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Architecture Matters: Protecting Data in a Mobile First, Cloud First World
Architecture Matters: Protecting Data in a Mobile First, Cloud First World
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 08 2018 05:59 AM
826
Views
Sep 08 2018
05:59 AM
Sep 08 2018
05:59 AM
First published on CloudBlogs on Feb 18, 2015
Over the past few months , I’ve written about why we believe Microsoft’s solutions are the most comprehensive and enterprise-ready. I’ve also written a lot about how we think our end-user experiences are the best in class with the Office mobile apps at the center – and our IT experiences are the best with the Enterprise Mobility Suite at the center. One of the things that I love about the Enterprise Mobility Management (EMM) space is the incredible pace of innovation – this space is evolving faster than any market I have worked in during my career. What was state of the art a year ago are table stakes today . Microsoft has brought a ton of innovation and value to the market in the last year that simply didn’t exist a year ago . For example, consider these things that didn’t exist a year ago: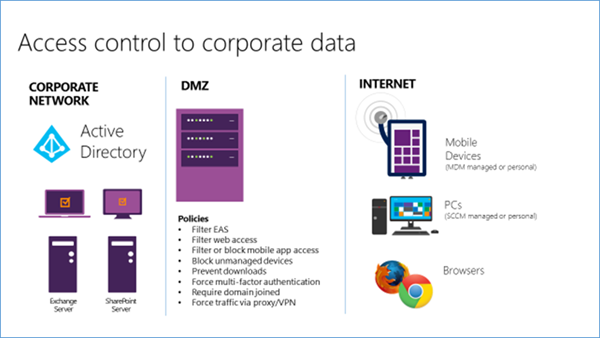 In the diagram above, you can see that corporate data (files, e-mail, etc.) live on servers in a corporate data center. Technology deployed at the perimeter helps limit access to that data. VPN concentrators, reverse proxies, application gateways and other perimeter technology enables customers to fine tune the circumstances under which access is given to corporate data by internet-connected devices and apps. This “walled garden” approach to access control works when you can force data through the controlled perimeter.
This is the most common way EMM vendors provide data protection and conditional access to corporate apps and data. In other words, all traffic from mobile devices is brought through perimeter (gateway) devices that are provided by the EMM vendor. The MDM and MAM (container) capabilities of the EMM vendor are integrated with the EMM vendor’s perimeter devices and, if a device does not meet a set of configuration criteria, communication from the devices is blocked at the edge of the network (aka conditional access).
So how does data protection and conditional access work in this configuration when your users start to use SaaS apps and data from the cloud – such as Office 365?
Short answer: It doesn’t!
In the diagram above, you can see that corporate data (files, e-mail, etc.) live on servers in a corporate data center. Technology deployed at the perimeter helps limit access to that data. VPN concentrators, reverse proxies, application gateways and other perimeter technology enables customers to fine tune the circumstances under which access is given to corporate data by internet-connected devices and apps. This “walled garden” approach to access control works when you can force data through the controlled perimeter.
This is the most common way EMM vendors provide data protection and conditional access to corporate apps and data. In other words, all traffic from mobile devices is brought through perimeter (gateway) devices that are provided by the EMM vendor. The MDM and MAM (container) capabilities of the EMM vendor are integrated with the EMM vendor’s perimeter devices and, if a device does not meet a set of configuration criteria, communication from the devices is blocked at the edge of the network (aka conditional access).
So how does data protection and conditional access work in this configuration when your users start to use SaaS apps and data from the cloud – such as Office 365?
Short answer: It doesn’t!
 In a SaaS model, the end-user device communicates directly with the SaaS app and never comes back through the company’s perimeter. Surprisingly, other EMM solutions cannot provide data protection and conditional access in this configuration.
A combination of on-premises and SaaS apps is the future
for most organizations – and you need an Enterprise Mobility solution that is built to do this!
Without this perimeter, you have to natively provide your access control and data containment in the devices, apps, and
in the cloud
(e.g.
multiple layers of protection
). That is a
simple and elegant
way to protect and maintain control over your data – and this is
exactly
how we’ve designed the
Enterprise Mobility Suite and Office 365 to work together
.
In a SaaS model, the end-user device communicates directly with the SaaS app and never comes back through the company’s perimeter. Surprisingly, other EMM solutions cannot provide data protection and conditional access in this configuration.
A combination of on-premises and SaaS apps is the future
for most organizations – and you need an Enterprise Mobility solution that is built to do this!
Without this perimeter, you have to natively provide your access control and data containment in the devices, apps, and
in the cloud
(e.g.
multiple layers of protection
). That is a
simple and elegant
way to protect and maintain control over your data – and this is
exactly
how we’ve designed the
Enterprise Mobility Suite and Office 365 to work together
.
 As you can see, Microsoft provides device management like every other vendor, and we integrate in the standard ways that organizations use to provide access to apps and data behind a firewall (VPN, per-app VPNs, etc.). What’s different is the way that
we took the cloud and SaaS into consideration
as we architected our solutions.
This different architecture means that our data protection and conditional access
live
in the cloud. The Intune component of EMS regularly writes to Azure Active Directory that the device is managed and it notes if the device is compliant or not. When an application (Outlook, the native e-mail app on iOS, Windows, Android) requests data from the service (Exchange, SharePoint, etc.) the service actually checks the AAD properties to see if the device is managed and compliant before the service sends any data back to the device. Really impressive.
The Office mobile apps like Word, Excel, PowerPoint, OneNote, and OneDrive for Business are available today in the iOS and Android stores – and they can integrate with Office 2013 on-premises and Office 365. It’s also worth noting that Lync is coming soon!
To answer the next obvious question
, yes, we are shipping the wrappers for your internal apps and SDKs for ISVs to use for their apps. This enables you to bring all of your apps into the same MAM solution as the Office mobile apps
and
deliver data protection and conditional access to your apps behind the firewall – and that includes your SaaS apps.
As I have talked with customers using other EMM solutions about this big difference, as well as the fact that the data protection and conditional access from them does not work against SaaS apps such as Office 365, they have reported back that they were advised by their EMM provider to deploy the Office 365 apps in a way that would route all traffic through DMZ proxies and gateways in order to go back out to the cloud. That is a
really
ineffective approach (and that was also a
really
long sentence). Not only does it introduce a lot of unnecessary latency, but it also fails to account for a use case where unmanaged devices or applications attempt to access cloud services. That’s not a great setup.
As you can see, Microsoft provides device management like every other vendor, and we integrate in the standard ways that organizations use to provide access to apps and data behind a firewall (VPN, per-app VPNs, etc.). What’s different is the way that
we took the cloud and SaaS into consideration
as we architected our solutions.
This different architecture means that our data protection and conditional access
live
in the cloud. The Intune component of EMS regularly writes to Azure Active Directory that the device is managed and it notes if the device is compliant or not. When an application (Outlook, the native e-mail app on iOS, Windows, Android) requests data from the service (Exchange, SharePoint, etc.) the service actually checks the AAD properties to see if the device is managed and compliant before the service sends any data back to the device. Really impressive.
The Office mobile apps like Word, Excel, PowerPoint, OneNote, and OneDrive for Business are available today in the iOS and Android stores – and they can integrate with Office 2013 on-premises and Office 365. It’s also worth noting that Lync is coming soon!
To answer the next obvious question
, yes, we are shipping the wrappers for your internal apps and SDKs for ISVs to use for their apps. This enables you to bring all of your apps into the same MAM solution as the Office mobile apps
and
deliver data protection and conditional access to your apps behind the firewall – and that includes your SaaS apps.
As I have talked with customers using other EMM solutions about this big difference, as well as the fact that the data protection and conditional access from them does not work against SaaS apps such as Office 365, they have reported back that they were advised by their EMM provider to deploy the Office 365 apps in a way that would route all traffic through DMZ proxies and gateways in order to go back out to the cloud. That is a
really
ineffective approach (and that was also a
really
long sentence). Not only does it introduce a lot of unnecessary latency, but it also fails to account for a use case where unmanaged devices or applications attempt to access cloud services. That’s not a great setup.

Over the past few months , I’ve written about why we believe Microsoft’s solutions are the most comprehensive and enterprise-ready. I’ve also written a lot about how we think our end-user experiences are the best in class with the Office mobile apps at the center – and our IT experiences are the best with the Enterprise Mobility Suite at the center. One of the things that I love about the Enterprise Mobility Management (EMM) space is the incredible pace of innovation – this space is evolving faster than any market I have worked in during my career. What was state of the art a year ago are table stakes today . Microsoft has brought a ton of innovation and value to the market in the last year that simply didn’t exist a year ago . For example, consider these things that didn’t exist a year ago:
-
Office for iPad
and
Android tablets
.
- And check out the great feedback the new Outlook apps and Office for Android Tablet apps are getting from The New York Times , GigaOm , Re/Code , PC World , GigaOm (again), Forbes , Fast Company , Business Insider , International Business Times , Windows SuperSite , Greenbot , and InformationWeek .
- The ability for the Office mobile apps to participate in a Mobile Application Management container .
- The reports now possible through EMS that help you identify and block so many of the cyber-attacks we are all reading about.
Cloud data protection as an example
It’s hard to overstate just how important data protection is to Enterprise Mobility. The biggest concerns around enterprise mobility revolve around governance, risk management, and compliance. There are well established norms in the industry for securing data on PCs; the norms for mobile devices and apps are still in the process of being canonized. The following diagram shows a common way that organizations protect corporate data today: In the diagram above, you can see that corporate data (files, e-mail, etc.) live on servers in a corporate data center. Technology deployed at the perimeter helps limit access to that data. VPN concentrators, reverse proxies, application gateways and other perimeter technology enables customers to fine tune the circumstances under which access is given to corporate data by internet-connected devices and apps. This “walled garden” approach to access control works when you can force data through the controlled perimeter.
This is the most common way EMM vendors provide data protection and conditional access to corporate apps and data. In other words, all traffic from mobile devices is brought through perimeter (gateway) devices that are provided by the EMM vendor. The MDM and MAM (container) capabilities of the EMM vendor are integrated with the EMM vendor’s perimeter devices and, if a device does not meet a set of configuration criteria, communication from the devices is blocked at the edge of the network (aka conditional access).
So how does data protection and conditional access work in this configuration when your users start to use SaaS apps and data from the cloud – such as Office 365?
Short answer: It doesn’t!
In the diagram above, you can see that corporate data (files, e-mail, etc.) live on servers in a corporate data center. Technology deployed at the perimeter helps limit access to that data. VPN concentrators, reverse proxies, application gateways and other perimeter technology enables customers to fine tune the circumstances under which access is given to corporate data by internet-connected devices and apps. This “walled garden” approach to access control works when you can force data through the controlled perimeter.
This is the most common way EMM vendors provide data protection and conditional access to corporate apps and data. In other words, all traffic from mobile devices is brought through perimeter (gateway) devices that are provided by the EMM vendor. The MDM and MAM (container) capabilities of the EMM vendor are integrated with the EMM vendor’s perimeter devices and, if a device does not meet a set of configuration criteria, communication from the devices is blocked at the edge of the network (aka conditional access).
So how does data protection and conditional access work in this configuration when your users start to use SaaS apps and data from the cloud – such as Office 365?
Short answer: It doesn’t!
The trend of moving to cloud-hosted services is real and it is accelerating
I thought think that one of the most interesting data points from Microsoft’s last quarterly earnings was the fact that 45% of all Office renewals decided to move to the cloud with Office 365 . Almost half of all renewals worldwide decided they were moving their e-mail (Exchange) and collaboration (SharePoint) to the cloud. Wow! So how do you provide data protection and conditional access to data in the cloud and with SaaS apps? In a SaaS model, the end-user device communicates directly with the SaaS app and never comes back through the company’s perimeter. Surprisingly, other EMM solutions cannot provide data protection and conditional access in this configuration.
A combination of on-premises and SaaS apps is the future
for most organizations – and you need an Enterprise Mobility solution that is built to do this!
Without this perimeter, you have to natively provide your access control and data containment in the devices, apps, and
in the cloud
(e.g.
multiple layers of protection
). That is a
simple and elegant
way to protect and maintain control over your data – and this is
exactly
how we’ve designed the
Enterprise Mobility Suite and Office 365 to work together
.
In a SaaS model, the end-user device communicates directly with the SaaS app and never comes back through the company’s perimeter. Surprisingly, other EMM solutions cannot provide data protection and conditional access in this configuration.
A combination of on-premises and SaaS apps is the future
for most organizations – and you need an Enterprise Mobility solution that is built to do this!
Without this perimeter, you have to natively provide your access control and data containment in the devices, apps, and
in the cloud
(e.g.
multiple layers of protection
). That is a
simple and elegant
way to protect and maintain control over your data – and this is
exactly
how we’ve designed the
Enterprise Mobility Suite and Office 365 to work together
.
At the risk of overstating this , I want to emphasize the difference between what we are doing at Microsoft and other EMM providers: I believe that EMS and O365 have been architected for the future – they are cloud architectures with a native understanding of what it means to operate powerfully in the cloud. This is simply not the case with the architecture of other solutions . They are built on the architecture of the past decade and do not understand the cloud and SaaS at the most basic, fundamental level.
Consider this setup:- A typical EMM solution starts with providing some fairly common MDM control over the devices.
- On top of that, the EMM provider will offer a MAM solution that includes a container. The container is a set of apps that behave in cooperation to manage and prevent data leakage. These apps offer mobile productivity solutions such as access to e-mail and files.
- This container is extended through a SDK or wrapper (a tool that will convert an existing app without using the SDK) which enables data leakage policies to extend from the EMM provider’s apps to apps delivered by ISVs and to the internal mobile line-of-business apps.
- The container is custom. Each EMM vendor today provides its own container and they are trying (unsuccessfully) to build an ecosystem around their containers.
- The EMM vendors are delivering their own productivity apps. These apps are notorious for what they don’t provide, e.g. the rich and incredible experience of Office (remember the Office mobile apps do not participate in any of these containers).
- The tight coupling of the custom data container to infrastructure in the DMZ. Doing this creates a clear challenge when you move your data and apps to the cloud. It simply doesn’t work.
 As you can see, Microsoft provides device management like every other vendor, and we integrate in the standard ways that organizations use to provide access to apps and data behind a firewall (VPN, per-app VPNs, etc.). What’s different is the way that
we took the cloud and SaaS into consideration
as we architected our solutions.
This different architecture means that our data protection and conditional access
live
in the cloud. The Intune component of EMS regularly writes to Azure Active Directory that the device is managed and it notes if the device is compliant or not. When an application (Outlook, the native e-mail app on iOS, Windows, Android) requests data from the service (Exchange, SharePoint, etc.) the service actually checks the AAD properties to see if the device is managed and compliant before the service sends any data back to the device. Really impressive.
The Office mobile apps like Word, Excel, PowerPoint, OneNote, and OneDrive for Business are available today in the iOS and Android stores – and they can integrate with Office 2013 on-premises and Office 365. It’s also worth noting that Lync is coming soon!
To answer the next obvious question
, yes, we are shipping the wrappers for your internal apps and SDKs for ISVs to use for their apps. This enables you to bring all of your apps into the same MAM solution as the Office mobile apps
and
deliver data protection and conditional access to your apps behind the firewall – and that includes your SaaS apps.
As I have talked with customers using other EMM solutions about this big difference, as well as the fact that the data protection and conditional access from them does not work against SaaS apps such as Office 365, they have reported back that they were advised by their EMM provider to deploy the Office 365 apps in a way that would route all traffic through DMZ proxies and gateways in order to go back out to the cloud. That is a
really
ineffective approach (and that was also a
really
long sentence). Not only does it introduce a lot of unnecessary latency, but it also fails to account for a use case where unmanaged devices or applications attempt to access cloud services. That’s not a great setup.
As you can see, Microsoft provides device management like every other vendor, and we integrate in the standard ways that organizations use to provide access to apps and data behind a firewall (VPN, per-app VPNs, etc.). What’s different is the way that
we took the cloud and SaaS into consideration
as we architected our solutions.
This different architecture means that our data protection and conditional access
live
in the cloud. The Intune component of EMS regularly writes to Azure Active Directory that the device is managed and it notes if the device is compliant or not. When an application (Outlook, the native e-mail app on iOS, Windows, Android) requests data from the service (Exchange, SharePoint, etc.) the service actually checks the AAD properties to see if the device is managed and compliant before the service sends any data back to the device. Really impressive.
The Office mobile apps like Word, Excel, PowerPoint, OneNote, and OneDrive for Business are available today in the iOS and Android stores – and they can integrate with Office 2013 on-premises and Office 365. It’s also worth noting that Lync is coming soon!
To answer the next obvious question
, yes, we are shipping the wrappers for your internal apps and SDKs for ISVs to use for their apps. This enables you to bring all of your apps into the same MAM solution as the Office mobile apps
and
deliver data protection and conditional access to your apps behind the firewall – and that includes your SaaS apps.
As I have talked with customers using other EMM solutions about this big difference, as well as the fact that the data protection and conditional access from them does not work against SaaS apps such as Office 365, they have reported back that they were advised by their EMM provider to deploy the Office 365 apps in a way that would route all traffic through DMZ proxies and gateways in order to go back out to the cloud. That is a
really
ineffective approach (and that was also a
really
long sentence). Not only does it introduce a lot of unnecessary latency, but it also fails to account for a use case where unmanaged devices or applications attempt to access cloud services. That’s not a great setup.
Conclusion
At Microsoft, we think mobile first, cloud first. That approach is core to both our culture , and our architecture . That guiding principle is reflected in our design, and it brings real, practical benefits for our customers – both in the short term and the long term. If you’re looking to deploy and use Office 365, take the time to evaluate deploying EMS along with it. We’ve built these two incredible sets of cloud services to seamlessly work together and deliver the data protection and performance you demand.
0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.