- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- What’s the best way to connect to Office 365 and Azure?
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
Customers moving to the cloud ask us two questions more than any others:
" What's the best way to connect my on-premises directory to Office 365?"
- and -
"What's the best way to connect my on-premises directory to Azure?"
Great questions.
The answer hinges on the fact that Office 365, Azure and many other Microsoft Cloud Services don't actually connect directly to your on-premises directory. They use Azure AD as their identity system, and it handles all the identity connections with your enterprise and your users. This specialization simplifies connecting to the cloud and means you can use a single connection to access multiple services from Microsoft and 3 rd parties.
As a result "How should I connect to Office 365?" (or Azure or CRM Online or PowerBI) is more accurately:
"How should my organization provision identities into Azure AD? And which authentication option should we use?"
Once this is answered, Office365, Azure, Microsoft CRM and PowerBI all "just work". Let's take a look at what the data tells us customers are actually doing.
Provisioning users into Azure AD:
To get started, as of this morning, 4.9M organizations are using Azure AD to manage > 430M identities:
- The majority of the 4.9M are smaller businesses and have < 500 employees.
-
A subset of the 4.9M organizations are medium/large and have 500 or more employees. Because these organizations are comparatively large, they account for 93% of identities in Azure AD.
- 55% of them are using Azure AD Sync (or its predecessor DirSync) to provision identities in Azure AD.
- 2% of them are using a 3rd party cloud identity service (i.e. Centrify, Okta, OneLogin, etc.) for provisioning.
- Another 2% use a wide variety of home grown and custom provisioning tools.
- The remainder are using one of our portals (Azure or Office365) and PowerShell scripts for provisioning.
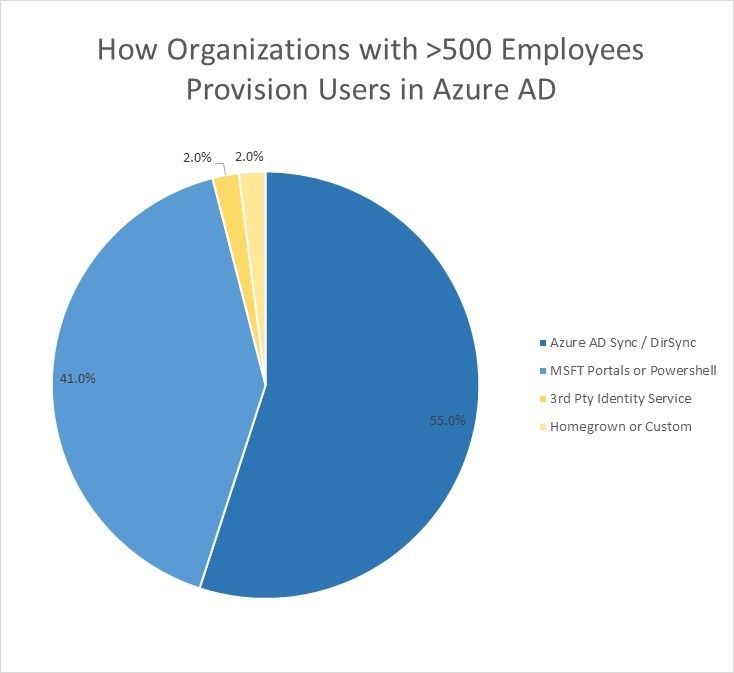
Fig 1: How organizations with >500 employees provision users in Azure AD
Authenticating with Azure AD:
If you follow this blog, you know that every day we process > 1 billion authentications and on our busiest days > 2 billion. Azure AD supports a variety of approaches to authentication, but a few of them are much more widely used than the others:
Of these 1B+ daily authentications
- 56% are cloud only and completed directly by Azure AD
- 32% are completed by an ADFS server deployed at a customer site
- 7% are completed using a password that was synced from on-premises using our Password Sync feature
- Just over 1% are completed by syndication partners (i.e. large companies who resell Microsoft services)
- Just under 1% are completed by a 3 rd third party federation server (i.e. CA Site Minder, Ping, etc.)
- Just under 1% are completed by a 3 rd party identity service (i.e. a company like Centrify, Okta, OneLogin, etc.)
-
The remaining 1% are completed with a variety of open source and custom solutions.
(Note: These don't sum to 100% due to rounding errors)

Fig 2: Breakdown of how Azure AD Authentications are completed
The numbers tell a clear story. We've designed Azure AD to be open and standards based so as to give our customers access to a wide variety of 3 rd party options. However the overwhelming majority of customers find that off-the-shelf AAD provides the best identity solution, eliminating added costs and the need to take dependencies.
Specifically:
-
For User Provisioning, they use either:
- Azure AD Sync or
- The Office 365 or Azure portals and PowerShell scripts
-
For authentication they use:
- Azure AD directly
- Active Directory Federation Server (ADFS) or
- The Password Sync feature of Azure AD Sync
We're thrilled to see this and happy to know that we're providing a complete solution that meets the needs of the vast majority of Microsoft's cloud customers!
If you found this blog post interesting/useful, please let me know. And as always, we'd love to receive any feedback or suggestions you have.
Best Regards,
Alex Simons (Twitter: @Alex_A_Simons )
Director of PM
Microsoft Identity and Security Services Division
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.