Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Announcing New Microsoft Enterprise Mobility Capabilities
Announcing New Microsoft Enterprise Mobility Capabilities
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 08 2018 07:48 AM
9,157
Views
Sep 08 2018
07:48 AM
Sep 08 2018
07:48 AM
First published on CloudBlogs on Nov 17, 2015
 The threats facing today’s organizations are far more complex, aggressive, and malicious than ever before. Even compared to just a few years ago, the threat landscape has rapidly evolved from unsophisticated mischief, to organized crime syndicates, to nation states intent on financial gain, IP theft, and terrorism.
Protecting against these constant threats is made even
more
difficult due to the basic fact that an increasing amount of an organization’s work is done beyond its traditional security perimeter.
This is what why the “
threat-scape
” has become increasingly hostile: Consider how common it is now for corporate data to live it’s entire life in the cloud and/or on mobile devices. It is no exaggeration to say that the perimeter as we once knew it (and the security that came with it) has evaporated!
These fundamental changes to the nature and philosophy of data security mean that every organization now needs a new approach if it expects to protect itself
and
meet the demands of their increasingly mobile and technically demanding workforce. Today's announcements in Washington D.C. enable
exactly
this. Satya detailed the end-to-end security of Microsoft and our partners which empowers users in our mobile-first, cloud-first world.
With cyberattacks becoming both more frequent and more severe, the security of any enterprise mobility strategy is more critical than ever. Organizations need to deploy technology that enables them to detect and respond to these increasingly sophisticated attacks.
In the past, your network perimeter was used to control access to corporate data. In a cloud-first, mobile-first world,
identity is the control plane
: You use it to control access to any service from any device, and you use it to get visibility and insight into
where
and
how
your data is being used.
In the past, point MDM solutions have attempted to manage your end users’ mobile productivity. These point solutions have required you to attempt to integrate a number of disjointed systems and your end-user experience has suffered as a result. We are taking a different approach:
We are building security and protection into all of our solutions vs. bolting them on afterwards
. The user experience is delivered from Office, the best in class for mobile productivity; IT gets the ability to natively define the policies for access control and data leakage prevention. All of this is natively enforced in the cloud fabric and on the mobile devices and apps. It’s a true
no-compromise solution
for infrastructure and protection.
Accomplishing this is the end result of many teams working together across Microsoft so that our products and services work together to
protect your company data at multiple layers
. This
multi-layered protection
is unique to Microsoft. It protects your organization at four distinct places: Identity, device, app, and data. The only way to execute this comprehensive integrated solution for productivity and protection is via Office 365 and the Enterprise Mobility Suite (EMS).
The threats facing today’s organizations are far more complex, aggressive, and malicious than ever before. Even compared to just a few years ago, the threat landscape has rapidly evolved from unsophisticated mischief, to organized crime syndicates, to nation states intent on financial gain, IP theft, and terrorism.
Protecting against these constant threats is made even
more
difficult due to the basic fact that an increasing amount of an organization’s work is done beyond its traditional security perimeter.
This is what why the “
threat-scape
” has become increasingly hostile: Consider how common it is now for corporate data to live it’s entire life in the cloud and/or on mobile devices. It is no exaggeration to say that the perimeter as we once knew it (and the security that came with it) has evaporated!
These fundamental changes to the nature and philosophy of data security mean that every organization now needs a new approach if it expects to protect itself
and
meet the demands of their increasingly mobile and technically demanding workforce. Today's announcements in Washington D.C. enable
exactly
this. Satya detailed the end-to-end security of Microsoft and our partners which empowers users in our mobile-first, cloud-first world.
With cyberattacks becoming both more frequent and more severe, the security of any enterprise mobility strategy is more critical than ever. Organizations need to deploy technology that enables them to detect and respond to these increasingly sophisticated attacks.
In the past, your network perimeter was used to control access to corporate data. In a cloud-first, mobile-first world,
identity is the control plane
: You use it to control access to any service from any device, and you use it to get visibility and insight into
where
and
how
your data is being used.
In the past, point MDM solutions have attempted to manage your end users’ mobile productivity. These point solutions have required you to attempt to integrate a number of disjointed systems and your end-user experience has suffered as a result. We are taking a different approach:
We are building security and protection into all of our solutions vs. bolting them on afterwards
. The user experience is delivered from Office, the best in class for mobile productivity; IT gets the ability to natively define the policies for access control and data leakage prevention. All of this is natively enforced in the cloud fabric and on the mobile devices and apps. It’s a true
no-compromise solution
for infrastructure and protection.
Accomplishing this is the end result of many teams working together across Microsoft so that our products and services work together to
protect your company data at multiple layers
. This
multi-layered protection
is unique to Microsoft. It protects your organization at four distinct places: Identity, device, app, and data. The only way to execute this comprehensive integrated solution for productivity and protection is via Office 365 and the Enterprise Mobility Suite (EMS).
 All of this is possible because of the years of deep integration between Office 365 and EMS. This solution is unique because it delivers this empowerment while simultaneously providing a secure work environment across all four of these scenarios.
Microsoft’s ability to solve for all of these scenarios in a way that is both empowering and secure is completely unique in the industry
. Being able to apply data leakage prevention policy regardless of MDM enrollment was the missing piece we’ve finalized to complete this matrix.
This means you can use these MAM capabilities in the Office mobile apps to help users protect the data being used in the apps – with or without the Intune MDM capabilities. This also means you can use the Intune MAM capabilities on a device that is managed by another MDM solution. This has been a common request: Organizations want to start using the Intune MAM and Office 365 capabilities immediately, but they know it is going to take a little time to migrate from the current MDM solution they have in place. The Intune-MAM-without-device-enrollment provides the solution for doing that.
All of this is possible because of the years of deep integration between Office 365 and EMS. This solution is unique because it delivers this empowerment while simultaneously providing a secure work environment across all four of these scenarios.
Microsoft’s ability to solve for all of these scenarios in a way that is both empowering and secure is completely unique in the industry
. Being able to apply data leakage prevention policy regardless of MDM enrollment was the missing piece we’ve finalized to complete this matrix.
This means you can use these MAM capabilities in the Office mobile apps to help users protect the data being used in the apps – with or without the Intune MDM capabilities. This also means you can use the Intune MAM capabilities on a device that is managed by another MDM solution. This has been a common request: Organizations want to start using the Intune MAM and Office 365 capabilities immediately, but they know it is going to take a little time to migrate from the current MDM solution they have in place. The Intune-MAM-without-device-enrollment provides the solution for doing that.

Summary:
Earlier today , in Washington DC, Satya spoke about Microsoft’s commitment to the security and management of enterprise devices and cloud apps. The threats facing today’s organizations are far more complex, aggressive, and malicious than ever before. Even compared to just a few years ago, the threat landscape has rapidly evolved from unsophisticated mischief, to organized crime syndicates, to nation states intent on financial gain, IP theft, and terrorism.
Protecting against these constant threats is made even
more
difficult due to the basic fact that an increasing amount of an organization’s work is done beyond its traditional security perimeter.
This is what why the “
threat-scape
” has become increasingly hostile: Consider how common it is now for corporate data to live it’s entire life in the cloud and/or on mobile devices. It is no exaggeration to say that the perimeter as we once knew it (and the security that came with it) has evaporated!
These fundamental changes to the nature and philosophy of data security mean that every organization now needs a new approach if it expects to protect itself
and
meet the demands of their increasingly mobile and technically demanding workforce. Today's announcements in Washington D.C. enable
exactly
this. Satya detailed the end-to-end security of Microsoft and our partners which empowers users in our mobile-first, cloud-first world.
With cyberattacks becoming both more frequent and more severe, the security of any enterprise mobility strategy is more critical than ever. Organizations need to deploy technology that enables them to detect and respond to these increasingly sophisticated attacks.
In the past, your network perimeter was used to control access to corporate data. In a cloud-first, mobile-first world,
identity is the control plane
: You use it to control access to any service from any device, and you use it to get visibility and insight into
where
and
how
your data is being used.
In the past, point MDM solutions have attempted to manage your end users’ mobile productivity. These point solutions have required you to attempt to integrate a number of disjointed systems and your end-user experience has suffered as a result. We are taking a different approach:
We are building security and protection into all of our solutions vs. bolting them on afterwards
. The user experience is delivered from Office, the best in class for mobile productivity; IT gets the ability to natively define the policies for access control and data leakage prevention. All of this is natively enforced in the cloud fabric and on the mobile devices and apps. It’s a true
no-compromise solution
for infrastructure and protection.
Accomplishing this is the end result of many teams working together across Microsoft so that our products and services work together to
protect your company data at multiple layers
. This
multi-layered protection
is unique to Microsoft. It protects your organization at four distinct places: Identity, device, app, and data. The only way to execute this comprehensive integrated solution for productivity and protection is via Office 365 and the Enterprise Mobility Suite (EMS).
The threats facing today’s organizations are far more complex, aggressive, and malicious than ever before. Even compared to just a few years ago, the threat landscape has rapidly evolved from unsophisticated mischief, to organized crime syndicates, to nation states intent on financial gain, IP theft, and terrorism.
Protecting against these constant threats is made even
more
difficult due to the basic fact that an increasing amount of an organization’s work is done beyond its traditional security perimeter.
This is what why the “
threat-scape
” has become increasingly hostile: Consider how common it is now for corporate data to live it’s entire life in the cloud and/or on mobile devices. It is no exaggeration to say that the perimeter as we once knew it (and the security that came with it) has evaporated!
These fundamental changes to the nature and philosophy of data security mean that every organization now needs a new approach if it expects to protect itself
and
meet the demands of their increasingly mobile and technically demanding workforce. Today's announcements in Washington D.C. enable
exactly
this. Satya detailed the end-to-end security of Microsoft and our partners which empowers users in our mobile-first, cloud-first world.
With cyberattacks becoming both more frequent and more severe, the security of any enterprise mobility strategy is more critical than ever. Organizations need to deploy technology that enables them to detect and respond to these increasingly sophisticated attacks.
In the past, your network perimeter was used to control access to corporate data. In a cloud-first, mobile-first world,
identity is the control plane
: You use it to control access to any service from any device, and you use it to get visibility and insight into
where
and
how
your data is being used.
In the past, point MDM solutions have attempted to manage your end users’ mobile productivity. These point solutions have required you to attempt to integrate a number of disjointed systems and your end-user experience has suffered as a result. We are taking a different approach:
We are building security and protection into all of our solutions vs. bolting them on afterwards
. The user experience is delivered from Office, the best in class for mobile productivity; IT gets the ability to natively define the policies for access control and data leakage prevention. All of this is natively enforced in the cloud fabric and on the mobile devices and apps. It’s a true
no-compromise solution
for infrastructure and protection.
Accomplishing this is the end result of many teams working together across Microsoft so that our products and services work together to
protect your company data at multiple layers
. This
multi-layered protection
is unique to Microsoft. It protects your organization at four distinct places: Identity, device, app, and data. The only way to execute this comprehensive integrated solution for productivity and protection is via Office 365 and the Enterprise Mobility Suite (EMS).
Today’s Announcement & New Capabilities in EMS:
Today announcements emphasize the importance we place on mobility innovations – both for productivity and security. In particular, today we announced that we’re delivering some new enhancements to Microsoft Intune . Intune already delivers mobile device and application management capabilities to ensure data and apps are protected on mobile devices. Now, Intune will provide expanded capabilities to manage company apps and data in many more cases, specifically:- Intune now provides data leakage prevention through its Mobile Application Management (MAM) features. Intune MAM was recently updated to isolate corporate and personal data within the same app – something no other solution provides. This means that users can use apps such as Office mobile to access their content from both personal locations ( e.g. OneDrive consumer) and corporate locations ( e.g. OneDrive for Business). When a corporate credential is used to access a document, additional controls are enforced that prevent that document from being leaked to a consumer app or service. This function is automatic and a part of the native app experience. Your users don’t have to use separate apps for work and personal use – they just use Office. This is a perfect example of identity providing the new perimeter (in this case, inside the mobile app itself).
- With today’s announcements, Intune’s MAM is being extended to “Bring your own” (BYO) devices that are not enrolled for device management (MDM). This protects company data in mobile apps without requiring IT to enroll and deeply manage that end users’ entire device. The end-user preserves complete control over their personal apps, data, and settings – while the IT department controls the protection of corporate IP.
- Intune MAM is also being extended to protect company information on devices enrolled into non-Microsoft MDM solutions. This allows you to start extending Intune MAM protections to mobile apps without having to first migrate your entire MDM solution.
- Additional Microsoft apps are announcing support of for Intune MAM, including Power BI, and Remote Desktop client (both of which are available now). Support for the Skype for Business and Dynamics CRM apps is coming soon.
- Major companies like Box and Adobe have announced iOS and Android apps with native support for Intune mobile application management. Additionally, SAP Fiori mobile apps that are customized and built by SAP’s customers using SAP’s Fiori mobile services will also support these management and data protection capabilities delivered by Microsoft Intune.
“The MAM features of Microsoft Intune will enable Nestlé employees to safely and securely access Office 365 from any device.” — Thomas Wildi, IT Strategy and Innovation, Nestlé
* * * * *
The primary applications used by organizations to create and share business data are the Office productivity apps: Outlook, Word, Excel, PowerPoint, Skype for Business, OneNote, OneDrive for Business, and Yammer (powered by the backend services of Exchange, SharePoint, Skype, and Yammer). To give you a data point from our telemetry on the massive and widespread usage of these apps, more than 70% of all attachments sent through Office 365 are Microsoft Office documents. Organizations all over the world are grappling with how to “Empower their users to be productive on the devices they love, while keeping the company data protected.” This challenge is our vision – it is the goal that teams across Microsoft are all working towards together when it comes to Enterprise Mobility. The challenges of providing great mobile productivity and protection represent a huge opportunity to help your organization achieve more. You can be an unmitigated hero if you successfully deliver the rich and empowering work environment your users want while also meeting your organization’s security requirements.Major Updates to our MDM/MAM Solution are Now Available in EMS, with Corresponding Updates to the Office Mobile Apps .
The combination of EMS and Office 365 is the industry’s premiere mobile productivity solution, and, with today’s announcements , this managed and protected work environment is available in many more scenarios. This is a significant step forward for the industry because organizations can now ensure that corporate apps and data are safe and secure no matter what type of device is being used. We are hearing from more and more customers that they want to focus their efforts on protecting the corporate apps and the corporate data without taking over the user’s device. There will be cases where organizations will want to manage at both the device and application layers, and there will be other cases where an organization will only want to manage the apps. The reality is that most organizations will actually do both, with app-focused management targeted at the BYO devices. The following list of Data Loss Protection capabilities are available to Intune MAM-enlightened apps without having to enroll and manage the device:- Corporate data can be selectively wiped, without impacting any personal data.
- We support controlling where corporate data can be saved to – either locally or to other services.
- The corporate data can be shared (cut/copy/paste) across the corporate apps freely (empowering the end-user) while preventing the sharing of corporate data into personal apps.
- We deliver a managed browser so that corporate browsing and web access is separate (and managed) from personal browsing.
- Word, Excel, PowerPoint, Outlook, OneNote, OneDrive for Business, and now Skype for Business are all being updated with these new capabilities. The data loss protection capabilities are natively built into the Office experience so that corporate data is seamlessly protected, independent of the MDM enrollment of the device.
- This is all built into the standard Office apps available in the Apple App Store or the Google Play store – there’s no wrapping or special apps required. All the end user has to do is authenticate to the app with their corporate credentials and then the data loss protection capabilities are automatically set up.
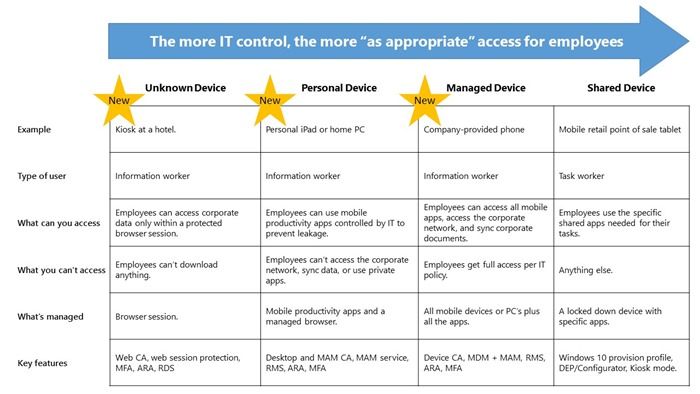
Expanding the User Scenarios to Include BYO and Unknown Devices
I love when I have the opportunity to sit down with technical leaders and dive into the scenarios that they are trying to enable within their organizations. One thing that has been incredibly intriguing (and maybe a little overwhelming) has been the breadth of scenarios that have to be considered in order to fully empower users on any device while keeping the company data protected . There are many ways in which users access and use data/content from Office 365 – these range from using the Office web apps on unknown devices ( e.g. a PC at a hotel or a convention), to using the Office mobile apps on corporate and personal devices, to using the full desktop apps on corporate and personal PCs that are domain joined. There is, obviously, a lot to think through in any of those scenarios. And, to fully address the breadth of these needs, there was a lot of work done here at Microsoft. The table below illustrates several different scenarios in detail, but here is a common scenario a single user may experience in a single day: An information worker begins her day reading corporate e-mail from a personal iPad while having breakfast at home. The new EMS capabilities help enable corporate e-mail to be securely accessed and protected on her personal device, as well as kept separate from the personal data on the device. This separation allows IT to apply data loss protection policies on the corporate apps and data without taking control of her personal device. When the worker arrives at work, she works on a corporate laptop. Because this laptop is a domain joined device and she has successfully authenticated, she is using the full Office desktop applications and has full access to the Office 365 services. (Side note: If a user is using a Windows 10 device, instead of using a password to authenticate they can use biometrics !) In the afternoon, she attends an industry event; wanting to travel light, she only carries her personal smart phone that has been MDM-enrolled and protected by the same Intune MAM capabilities as her personal iPad. While at the event, the she gets an e-mail requesting some urgent work that requires accessing and editing a confidential Word document. She is able to complete that work from a PC at the event using the Word web app or using the full Office apps remoted to her via Azure RemoteApp. Pretty amazing. All of this is possible because of the years of deep integration between Office 365 and EMS. This solution is unique because it delivers this empowerment while simultaneously providing a secure work environment across all four of these scenarios.
Microsoft’s ability to solve for all of these scenarios in a way that is both empowering and secure is completely unique in the industry
. Being able to apply data leakage prevention policy regardless of MDM enrollment was the missing piece we’ve finalized to complete this matrix.
This means you can use these MAM capabilities in the Office mobile apps to help users protect the data being used in the apps – with or without the Intune MDM capabilities. This also means you can use the Intune MAM capabilities on a device that is managed by another MDM solution. This has been a common request: Organizations want to start using the Intune MAM and Office 365 capabilities immediately, but they know it is going to take a little time to migrate from the current MDM solution they have in place. The Intune-MAM-without-device-enrollment provides the solution for doing that.
All of this is possible because of the years of deep integration between Office 365 and EMS. This solution is unique because it delivers this empowerment while simultaneously providing a secure work environment across all four of these scenarios.
Microsoft’s ability to solve for all of these scenarios in a way that is both empowering and secure is completely unique in the industry
. Being able to apply data leakage prevention policy regardless of MDM enrollment was the missing piece we’ve finalized to complete this matrix.
This means you can use these MAM capabilities in the Office mobile apps to help users protect the data being used in the apps – with or without the Intune MDM capabilities. This also means you can use the Intune MAM capabilities on a device that is managed by another MDM solution. This has been a common request: Organizations want to start using the Intune MAM and Office 365 capabilities immediately, but they know it is going to take a little time to migrate from the current MDM solution they have in place. The Intune-MAM-without-device-enrollment provides the solution for doing that.
An Expanding EMS Ecosystem
One of the things that makes me the most excited about the value we are delivering to our users is the integrated end-to-end scenarios that stretch across Microsoft. The depth of this integration is incredible :- EMS components are deeply integrated.
- EMS is deeply integrated with System Center Configuration Manager and Active Directory (carrying forward your existing investments).
- EMS is deeply integrated with Office 365.
- EMS is deeply integrated with Windows 10.
We are Also Announcing Leading Companies Integrating with EMS:
Let’s start with some the key partners who are (or will shortly be) joining us on our journey to provide rich productivity experiences with applications integrated with EMS/Intune MAM capabilities:- Adobe Click here to learn more about when and how to get the app for Intune MAM
- Box Click here to learn more about when and how to get the app for Intune MAM
- SAP Fiori apps Click here to learn more about when and how to create the custom apps with Intune support
- Acronis Click here to learn more about when and how to get the app for Intune MAM
- Citrix Click here to learn more about when and how to get the app for Intune MAM
- Foxit Click here to learn more about when and how to get the app for Intune MAM
Game Changing Announcements
This is truly a game changing set of announcements. Organizations are searching for the solution that enables them to deliver an empowering work environment for their users while keeping the corporate data protected – across all of their usage scenarios. This challenge is made all the more complex as the security threats we all face become more sophisticated and more targeted. The combined solution of Office 365 + EMS, along with the broad collection of Microsoft apps across all the key OS platforms, is both unique and the most complete and comprehensive solution for empowering your users, on any device, with or without MDM. Simply incredible.Here are some great ways to get started with our new capabilities:
- Learn more about the Intune capabilities .
- Learn how to take advantage of these new capabilities.
- Go here to learn how you can integrate your app with Intune.
- Learn more about the EMS offering.
- Try EMS for free !
- Want to really get to know EMS? Check out this deep dive video: aka.ms/GetToKnowEMS .

0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.