- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- New series: The Azure AD Mailbag
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
First published on CloudBlogs on Dec, 04 2015
Hi everyone, I'm Sean Ivey. You might know me from an onsite visit, or possibly from reading a few articles on the AskDS blog . I recently joined the Azure Active Directory Customer Success Team. Our team is responsible for the integration with software as a service (SaaS) apps with Azure AD. This week we'll focus on SaaS (and other application) questions we've seen that will help as you start or continue your adoption of Azure AD! If our readers find these helpful let us know in the comments or on twitter at @MarkMorow and @Alex_A_Simons . Let's get started.
Question: In the Azure AD App portal I'm able to add both Salesforce and Salesforce Sandbox. I'm able to configure Salesforce by following this link. When I try the same thing for Salesforce Sandbox it doesn’t work. How do I configure Salesforce Sandbox?
Answer: There are actually different configuration steps that need to be done for a Salesforce Sandbox instance. Take a read through this tutorial and see if that doesn't get it going for you.
Question: Can I configure my on-premises SharePoint 2013 farm as a custom (bring your own app) app and share it with B2B users?
Answer: Yes, but you'll need a federation service to do the transition from the token that Azure Active Directory creates to one SharePoint 2013 can consume. The easiest way to configure this is to setup Azure AD as a claims provider in AD FS, and then setup the SharePoint 2013 farm as a relying party to AD FS.
To setup Azure AD as a claims provider in AD FS:
1. Create a custom application in Azure AD (additional info here).
2. Configure SSO for the application
- Microsoft Azure AD Single Sign-On should be selected here:
- Check "Show advanced settings" on the second screen
- Fill out the Sign On URL as the URL to the SharePoint website
- Add the Issuer URL of the AD FS farm
- Add the Reply URL of the AD FS farm
- In step 3 click "Download Metadata (XML)". This will be used on the AD FS server to add Azure AD as the claims provider.
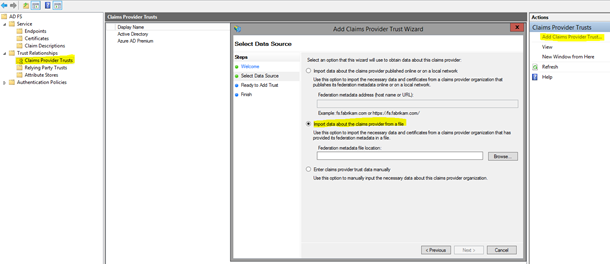
3. On the AD FS server, add a claims provider trust and select the second option to "Import data…" Here you will import the XML file that was previously downloaded.
Once this is finished, the SharePoint farm needs to be setup for claims based authentication and set to use AD FS for authentication. You can read more about that here . Setting it up this way will cause AD FS to perform the transition from the SAML 2.0 token that Azure AD issues to WS-Fed using a SAML 1.1 token for SharePoint to consume. This can be used in conjunction with Azure App Proxy so the SharePoint site can be accessed externally without the need to open any ports! When configuring SharePoint 2013 like this for your B2B users, all of the benefits a typical SaaS app gets are exposed, such as conditional access rules and self-service access assignment.
Question: When we add a SaaS app from the gallery, some apps show the federation option and some of them do not, why?
Answer: Azure AD supports three different ways to sign in to applications. Only tested federated application will show the federation option.
- Federated Single Sign-On enables applications to redirect to Azure AD for user authentication instead of prompting for its own password. This is supported for applications that support protocols such as SAML 2.0, WS-Federation, or OpenID Connect, and is the richest mode of single sign-on.
- Password-based Single Sign-On enables secure application password storage and replay using a web browser extension or mobile app. This leverages the existing sign-in process provided by the application, but enables an administrator to manage the passwords and does not require the user to know the password.
- Existing Single Sign-On enables Azure AD to leverage any existing single sign-on that has been set up for the application, but enables these applications to be linked to the Office 365 or Azure AD access panel portals, and also enables additional reporting in Azure AD when the applications are launched there.
Additional information can be found here .
Question: Which protocols are supported for Single Sign On?
Answer: Azure AD supports SAML 2.0, Open ID Connect, OAuth 2.0 and WS-Fed protocols for federation.
Question: What should I do if I don’t find my required application in the gallery?
Answer: Azure AD now provides the Bring Your Own App feature for enabling SSO if the SaaS app supports SAML 2.0 protocol. Please note that this feature is supported for SAML protocol integrations. You can also reach out to your CSV and request them to get added in Azure AD Marketplace. We welcome all the CSV teams to add their application in the gallery. For more information, please visit this page and submit your request to the waadpartners@microsoft.com alias as mentioned in the article. -Sean Ivey, Aaron Smalser, Jeevan Desarda, and Mark Morowczynski
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.