- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Advanced Threat Analytics Event Log Collection
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Network traffic collection is the main data source Advanced Threat Analytics (ATA) uses to detect threats and abnormal behavior. It also analyzes event log ID 4776 , and will likely collect additional events in the future. This is why we’re devoting a topic to understanding methods and configuration for event collection. You can configure the ATA gateway, both lightweight and standalone, to collect the event via a syslog listener and/or using Windows Event Forwarding (WEF). We recommend using the syslog listener if a SIEM is available and supported. If a supported SIEM is unavailable, you would use WEF. SIEM Today, ATA supports four SIEM products: RSA Security Analytics, HP ArcSight, Splunk, and IBM QRadar. The SIEM needs to collect the 4776 event from all Domain Controllers (DC) ATA is monitoring. You need to configure the SIEM to then forward the collected 4776 event from the DCs to an ATA gateway. You can forward all 4776 events from all DCs to a single gateway in the ATA deployment. The gateway will receive the events, process them and send them to the ATA center. If you have 100% standalone gateways or a mixed gateway deployment, forward the events to a standalone gateway close to the SIEM. The following diagram depicts this configuration, which ensures the load is put on a dedicated server vs. a domain controller.


Windows Event Forwarding Windows Event Forwarding is a built-in technology that allows you to collect events from Windows operating systems. You can read some basic primers on WEF here and here . Leverage WEF when you don’t have a supported SIEM in the environment to collect the 4776 event and forward it. WEF can use collector-initiated (pull) or source-initiated (push) subscriptions to get the events from the DCs. Lightweight Gateway—Collector-Initiated For lightweight gateways, we recommend a collector-initiated subscription configured on the domain controller. Collector-initiated means the subscription will pull the events from the endpoint. The subscription and the endpoint are the same host, so neither the collector nor the endpoint will utilize any network resources. You will need to configure the subscription on each lightweight gateway, which you can script with wecutil.exe. To script this configuration for LWGWs, you will need a template XML file. Here is a sample you can use: <?xml version="1.0" encoding="UTF-8"?> <Subscription xmlns=" http://schemas.microsoft.com/2006/03/windows/events/subscription ">
<SubscriptionId>ATA-4776</SubscriptionId>
<SubscriptionType>CollectorInitiated</SubscriptionType>
<Description></Description>
<Enabled>true</Enabled>
<Uri> http://schemas.microsoft.com/wbem/wsman/1/windows/EventLog</Uri >
<ConfigurationMode>Normal</ConfigurationMode>
<Delivery Mode="Pull">
<Batching>
<MaxLatencyTime>900000</MaxLatencyTime>
</Batching>
<PushSettings>
<Heartbeat Interval="900000"/>
</PushSettings>
</Delivery>
<Query>
<![CDATA[
<QueryList><Query Id="0"><Select Path="Security">*[System[(EventID=4776)]]</Select></Query></QueryList> ]]></Query>
<ReadExistingEvents>false</ReadExistingEvents>
<TransportName>HTTP</TransportName>
<TransportPort>5985</TransportPort>
<ContentFormat>RenderedText</ContentFormat>
<Locale Language="en-US"/>
<LogFile>ForwardedEvents</LogFile>
<PublisherName>Microsoft-Windows-EventCollector</PublisherName>
<CredentialsType>Default</CredentialsType>
<EventSources>
<EventSource Enabled="true">
<Address>lwgw.contoso.com</Address>
</EventSource>
</EventSources>
</Subscription> Here is the sample PowerShell to create the subscription based on the template.Import-Module ActiveDirectory
#Copy the template locally
$FileLocation = “\\server\share”
Copy-Item $FileLocation\ATA-4776.xml $ENV:TEMP
#Configure WinRM
winrm qc -quiet
#configure WinEvent Collection service
wecutil.exe qc /q:true
#Get Computer SID
$strDNSName = (Get-ADComputer $ENV:Computername).DNSHostName
#Replace the SID in the temp XML
(Get-Content "$ENV:TEMP\ATA-4776.xml") -replace 'lwgw.contoso.com', "$strDNSName"| Set-Content "$ENV:TEMP\ATA-4776.xml"
#Configure the Subscription
wecutil.exe cs "$ENV:TEMP\ATA-4776.xml"
Gateway—Source-Initiated For domain controllers monitored by gateways, we recommend configuring a source-initiated subscription on the gateway to receive the events from the DCs. You will need to configure the DCs with a subscription manager group policy setting. You can target the subscription manager at the respective DCs using security filtering. Here are some screen shots of subscription manager configuration found under Computer Policy \ Administrative Templates \ Windows Components \ Event Forwarding – Configure Target Subscription Manager
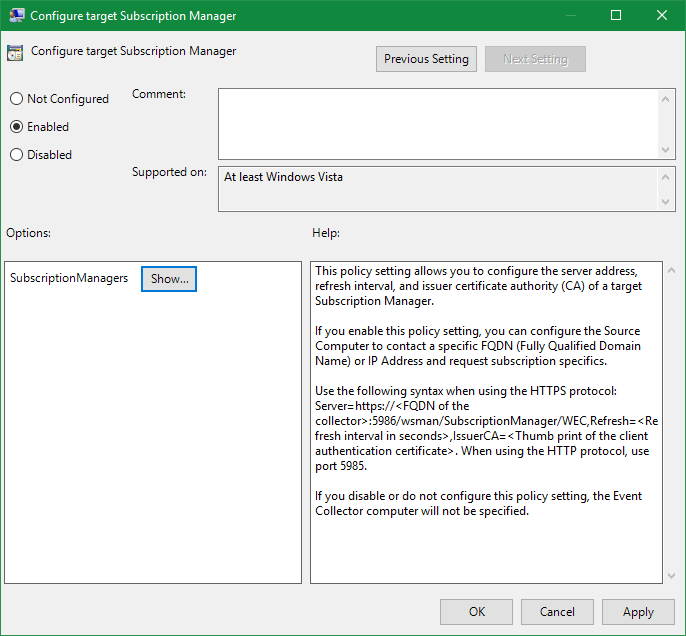
 To recap, we recommend:
To recap, we recommend:
- DCs with LWGW use a local collector-initiated subscription.
- DCs monitored by a GW use a source-initiated subscription.
 For questions or feedback contact
me
directly:
Nicholas DiCola
ndicola@microsoft.com
Principal Program Manager
C+E Security CxP Team
For questions or feedback contact
me
directly:
Nicholas DiCola
ndicola@microsoft.com
Principal Program Manager
C+E Security CxP Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.