Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- PingAccess for Azure AD: The public preview is being deployed!
PingAccess for Azure AD: The public preview is being deployed!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 07 2018 08:42 AM
6,401
Views
Sep 07 2018
08:42 AM
Sep 07 2018
08:42 AM
First published on CloudBlogs on Mar, 22 2017
Howdy folks, Back in September, I blogged about our exciting partnership with Ping Identity . Since then, Microsoft and Ping Identity have worked closely together to extend the capabilities of Azure AD Application Proxy to support new kinds of on-premises applications using Ping Access. I'm happy to announce today that PingAccess for Azure AD is now ready for Public Preview and is currently being deployed across Azure AD data centers around the world. Many of you in North America will see it turn on today and it should be available to everyone by the end of the day Friday, 3/24/2017. I've invited one of the program managers on our team, Harshini Jayaram, to share more details in a blog, which you'll find below. We hope you try it out and look forward to hearing what you think! Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division ---- Hi all, We've already have many customers use Application Proxy to provide single sign-on (SSO) and secure remote access for web applications hosted on-premises. Many of them use this product for applications such as local SharePoint sites, Outlook Web Access for local Exchange servers, and other business web applications. It is a simple, secure, and cost-effective solution:
Howdy folks, Back in September, I blogged about our exciting partnership with Ping Identity . Since then, Microsoft and Ping Identity have worked closely together to extend the capabilities of Azure AD Application Proxy to support new kinds of on-premises applications using Ping Access. I'm happy to announce today that PingAccess for Azure AD is now ready for Public Preview and is currently being deployed across Azure AD data centers around the world. Many of you in North America will see it turn on today and it should be available to everyone by the end of the day Friday, 3/24/2017. I've invited one of the program managers on our team, Harshini Jayaram, to share more details in a blog, which you'll find below. We hope you try it out and look forward to hearing what you think! Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division ---- Hi all, We've already have many customers use Application Proxy to provide single sign-on (SSO) and secure remote access for web applications hosted on-premises. Many of them use this product for applications such as local SharePoint sites, Outlook Web Access for local Exchange servers, and other business web applications. It is a simple, secure, and cost-effective solution:
- Simple: You don't need to change the network infrastructure, put anything in a DMZ, or use VPN.
- Secure: Application Proxy only uses outbound connections, giving you a more secure solution. It also works with other security features you've seen in Azure such as two-step verification, conditional access, and risk analysis. Learn more about this in Security considerations for Azure AD Application Proxy .
- Cost-Effective: Application Proxy is a service that we maintain in the cloud, so you can save time and money.
- Web applications using Integrated Windows Authentication
- Web applications using form-based access
- Web APIs that you want to expose to rich applications on different devices
- Applications hosted behind a Remote Desktop Gateway
PingAccess for Azure AD enables more apps!
Our customers have consistently asked for Application Proxy to also support apps that use headers for authentication, such as Peoplesoft, Netweaver Portal, and WebCenter. To enable this capability for our Azure AD Premium customers, we have partnered with Ping Identity. Ping Identity's PingAccess now allows Application Proxy to support apps that use header-based authentication. PingAccess is installed on-premises. For apps that use header-based authentication, Application Proxy connectors route traffic through PingAccess. Existing App Proxy applications are not impacted and use the current flow with no changes. An overview of this flow is shown below, and you can always check out our overview documentation for more on App Proxy flows.
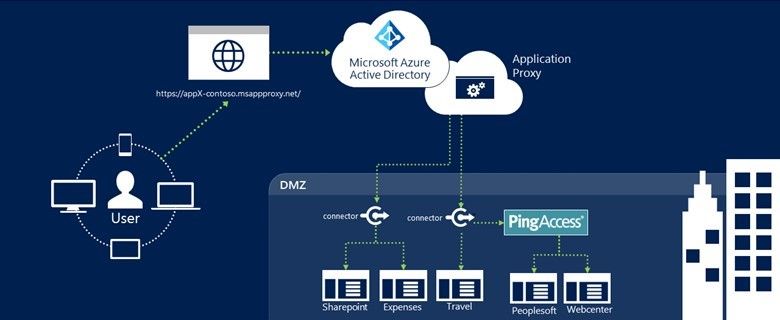
Figure 1 : Application Proxy + PingAccess Infrastructure Overview
PingAccess is a separately licensed feature, but your Azure Premium licenses now include a free license to configure up to 20 applications with this flow. If you have more apps, you'll need to get a license through Ping Identity.Joining the Preview
We are excited to have you join our preview! To get started you need to:- Configure Application Proxy Connectors
- Create an Azure AD Application Proxy Application
- Download & Configure PingAccess
- Configure Applications in PingAccess
0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.