Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- How Microsoft EMS can support you in your journey to EU GDPR compliance – Part 6
How Microsoft EMS can support you in your journey to EU GDPR compliance – Part 6
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 08 2018 10:23 AM
8,646
Views
Sep 08 2018
10:23 AM
Sep 08 2018
10:23 AM
First published on CloudBlogs on Aug 07, 2017
The General Data Protection Regulation (GDPR) strengthens the right of individuals in the European Union (EU) to control their personal data and requires organizations to bolster their privacy and data protection measures. Enterprise Mobility + Security (EMS) technologies may help you meet these new requirements. In the whitepaper “ Beginning Your GDPR Journey ,” we introduced five key use case scenarios relevant to data protection, where Microsoft Enterprise Mobility + Security (EMS) technologies may provide critical support: Traditional IT security tools provide limited protection against sophisticated cybersecurity attacks when user credentials are stolen. Initial set up, creating rules, and fine-tuning are cumbersome and may take years. Every day, you may receive several reports full of false positives.
Most of the time, you may not have the resources to review this information, and even if you could, you may still not have the answers. These tools are designed to protect the perimeter, and are primarily designed to stop attackers from gaining access.
Traditional IT security tools provide limited protection against sophisticated cybersecurity attacks when user credentials are stolen. Initial set up, creating rules, and fine-tuning are cumbersome and may take years. Every day, you may receive several reports full of false positives.
Most of the time, you may not have the resources to review this information, and even if you could, you may still not have the answers. These tools are designed to protect the perimeter, and are primarily designed to stop attackers from gaining access.

The General Data Protection Regulation (GDPR) strengthens the right of individuals in the European Union (EU) to control their personal data and requires organizations to bolster their privacy and data protection measures. Enterprise Mobility + Security (EMS) technologies may help you meet these new requirements. In the whitepaper “ Beginning Your GDPR Journey ,” we introduced five key use case scenarios relevant to data protection, where Microsoft Enterprise Mobility + Security (EMS) technologies may provide critical support:
- How to provide persistent data protection on-premises and in the cloud
- How to grant and restrict access to data
- How to gain visibility and control of data in cloud apps
- How to protect data in mobile devices and applications
- How to detect data breaches before they cause damage
 Traditional IT security tools provide limited protection against sophisticated cybersecurity attacks when user credentials are stolen. Initial set up, creating rules, and fine-tuning are cumbersome and may take years. Every day, you may receive several reports full of false positives.
Most of the time, you may not have the resources to review this information, and even if you could, you may still not have the answers. These tools are designed to protect the perimeter, and are primarily designed to stop attackers from gaining access.
Traditional IT security tools provide limited protection against sophisticated cybersecurity attacks when user credentials are stolen. Initial set up, creating rules, and fine-tuning are cumbersome and may take years. Every day, you may receive several reports full of false positives.
Most of the time, you may not have the resources to review this information, and even if you could, you may still not have the answers. These tools are designed to protect the perimeter, and are primarily designed to stop attackers from gaining access.
Uncover suspicious activity and pinpoint threats
Microsoft Advanced Threat Analytics (ATA) is an on-premises solution that leverages deep packet inspection (DPI) technology to analyze network traffic, as well as data from your SIEM and Active Directory. ATA analyzes this information to create dynamic behavioral profiles for each entity in your organization and builds an Organizational Security Graph (an entity interaction visual map representing the context and activities of users, devices and resources). After building an interaction map, ATA identifies abnormal behavior of entities, as well as advanced attacks and security risks, without the need to create rules, policies, or install desktop and server agents. Microsoft Advanced Threat Analytics focuses on detecting the following suspicious behaviors:- Abnormal behavior : ATA uses Machine Learning algorithms to identify normal and abnormal entity behavior and will detect anomalous logins, abnormal resource access, and even unusual working hours.

Advanced Threat Analytics – Abnormal User Behavior Alert
- Advanced attacks in near real-time based on TTPs : ATA uses Deep Packet Inspection technology and information from other sources to identify advanced attacks such as Pass-the-Hash, Pass-the-Ticket, Overpass-the-Hash, Forged PAC, Golden Ticket, and Remote Execution on the Domain Controllers, Skeleton Key Malware, Honey token activities and more.
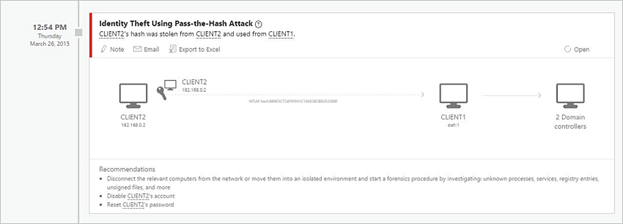
- Known security issues and risks : ATA identifies known security issues and risks such as service account exposed passwords in cleartext over the network, broken trust, weak protocols and other protocol vulnerabilities.
Advanced Threat Analytics – Detection of Known Security Issues
The constant reporting of traditional security tools and the need to sift through them to locate the important and relevant alerts can be overwhelming. ATA provides an attack timeline - a clear, efficient, and convenient feed that surfaces the right things in a visual timeline, giving you the power of perspective on the who, what, when, and how. ATA also provides recommendations for investigation and remediation for each suspicious activity.As always, the team at Microsoft encourages to you explore further:
- Understand Microsoft Advanced Threat Analytics and how it works in this video
- Download our Whitepaper to understand how EMS can support your GDPR compliance journey
- Read additional content on the Microsoft GDPR Website
- Try Microsoft Advanced Threat Analytics for Free to explore the features we’ve discussed
0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
