
Hyperlight Wasm: Fast, secure, and OS-free
We're announcing the release of Hyperlight Wasm: a Hyperlight virtual machine “micro-guest”…

Traditional security processes can often become a roadblock when delivering software via DevOps processes at the rate that today’s business world demands. Today, security is not just the responsibility of the security teams—it is a shared responsibility among all the teams in the applications lifecycle. This integration is known as DevSecOps. DevSecOps is not about slowing progress or sacrificing agility gained through DevOps. Rather, DevSecOps promotes a collaborative approach to security so that it becomes a central part of the application lifecycle.
At the same time, the modernization of infrastructure and applications is driving the rapid growth of containers and container orchestration platforms as a part of DevOps. The most popular orchestration platform for running containers is Kubernetes. Results from the RightScale 2019 State of the Cloud Report show that “Container use is up, and Kubernetes use is skyrocketing. The use of Docker containers continues to grow, with adoption increasing to 57 percent from 49 percent in 2018. Kubernetes achieving even faster growth, increasing from 27 percent to 48 percent adoption.”
As companies start to adopt Kubernetes, it’s critical to incorporate DevSecOps best practices, especially because container applications have multiple layers of abstraction. With container technology, you have an orchestration platform, host OS, container runtime, container images, container registry, and the running containers—all of which need to be secured in order to avoid risks like deficient authorization/authentication, bugs, and misconfiguration.
Let’s look at the risk areas of containers and Kubernetes along with the DevSecOps best practices that help mitigate them.
First, let’s address the two most common security risks for containerization: the container images themselves and the container registries.
Risks for container images include clear-text secrets, embedded malware, insecure software or libraries, bugs, outdated/stale images, and the use of untrusted images. There are several ways you can secure images:
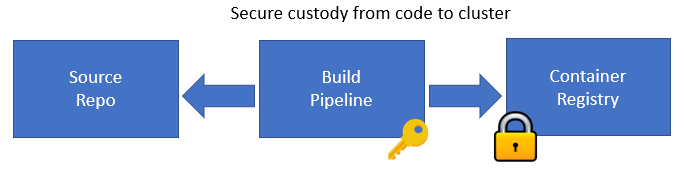
The second most common security risks in containerization are threats to container registries. These risks include insecure connections to registries, deficient authorization/authentication restrictions, and outdated/stale images. To boost security, you can leverage group isolation through nested namespaces, segmenting image access to specific teams in your organization.
Another isolation technique is to deploy the registry in a dedicated virtual network (VNet). In a dedicated VNet, such as Azure VNet, only users and resources in that VNet can access the registry.
As an example, let’s take a closer look at what Azure Container Registry (ACR) offers. ACR has two authentication methods: individual identity authentication (IIA) and headless/service identity authentication. IIA has an az acr login (via Docker CLI) used by developers to pull and push registry images. Headless authentication uses a service principle used in CI/CD pipelines. Limit the use of individual identity authentication to a small group of users and follow standard user account best practices.
By granting trusted image push permission to select users, you can limit who can push images to your container registry. Again, use a DevOps capability such as Azure DevOps to keep container images up to date. And finally, enable content trust on your container registry so you can enforce using only signed container images.
Authentication and authorization are at the core of securing cloud and DevOps. Authentication is confirming the identity of a user and authorization is the act of verifying and allowing access to resources. Think of these two as AuthN vs AuthZ.

Securing authentication and authorization is important to your container registry and other containerization components like the cluster and CI/CD pipeline. Azure Active Directory (AAD) helps centralize identity and access management to services running in Azure. AAD comes with many features that help with security, including privileged identity management (PIM), multi-factor authentication, service principal accounts, conditional access, and more. AAD extends authentication and access controls with the container registry, the cluster, and even a pipeline in Azure DevOps.
Here are some tips for securing authentication and authorization:
Azure Kubernetes Service also enables you to limit access for not only the resources and people, but also the content of the incoming requests. Operators can select from a predefined set of Azure policies and assign them to AKS clusters. This enables deploy-time enforcement of organizational policies. For example, any resources that are currently deployed to AKS can be checked for compliance with the assigned policies and if found to be non-compliant, the violations are reported so appropriate action can be taken to rectify. Similarly, if a user tries to create resources that are not compliant with policy, his or her requests are denied and the user is presented with a message detailing the policy that caused the denial.
As a part of security, it is important to perform monitoring and have alerting around the state of security in DevOps and cloud. Alerting and monitoring in DevSecOps should include the following: unified pane of glass of security across the DevOps stages, visibility and ability to control the status for enterprise application resources in Azure subscriptions, and actionable alerts for security drift.
With the changing landscape of modern technologies—including containers, Kubernetes, and DevOps—it’s important to keep security top-of-mind and to shift security left by adopting a DevSecOps mindset. As you embark on your container and Kubernetes journey with AKS, refer to this blog post for things you can do to secure your Kubernetes clusters and container images.
For more information on DevSecOps with Microsoft and AKS, check out the following resources:
Notifications