Today, we are excited to announce an open-source project called Azure AD workload identity for Kubernetes. It leverages the public preview capability of Azure AD workload identity federation. With this project, developers can use native Kubernetes concepts of service accounts and federation to access Azure AD protected resources, such as Azure and Microsoft Graph, without needing secrets.
The existing Azure AD Pod Identity project addresses this need. However, the Azure AD workload identity approach is simpler to use and deploy, and overcomes several limitations in Azure AD Pod Identity:
- Removes the scale and performance issues that existed for identity assignment.
- Supports Kubernetes clusters hosted in any cloud.
- Supports both Linux and Windows workloads.
- Removes the need for Custom Resource Definitions and pods that intercept IMDS (Instance Metadata Service) traffic.
- Avoids the complication and error-prone installation steps such as cluster role assignment.
How does this work?
As shown in the following graphic, the Kubernetes cluster becomes a token issuer, issuing tokens to Kubernetes Service Accounts. These tokens can be configured to be trusted on Azure AD applications. They can then be exchanged for an Azure AD access token using the Azure Identity SDKs or the Microsoft Authentication Library (MSAL).
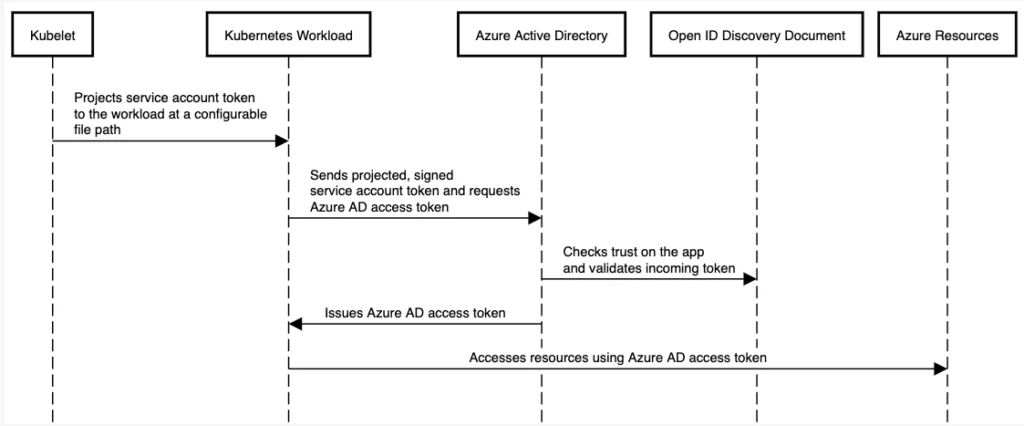
To learn more, see the documentation in the Azure Workload Identity open-source project. See also the Azure AD documentation for workload identity federation for an overview.
What is next?
Azure AD workload identity federation for Kubernetes is currently supported only on Azure AD applications. We intend to extend the same model for Azure managed identities.
In the coming months, we plan to replace Azure AD Pod Identity with Azure Workload Identity. Our goal is to equip users who are already using Azure AD Pod Identity to move to Azure Workload Identity with minimal changes.
We appreciate all input from the community. Please share any feedback or questions via GitHub issues or discussions. Your support will help shape the project to meet community needs for ensuring secure access to Azure AD protected resources from Kubernetes workloads.
