
Register now for the Microsoft Windows Server Summit 2024
Stay ahead of the curve and learn about the latest innovations and best practices in the world of Windows Server. Join us March 26 to 28, 2024…



This blog post was authored by Dean Wells, Principal Program Manager, Windows Server.
In the preceding blogs, you were given a video-tour of some of the high-level advancements made in Windows Server 2019 that touched on areas such as the improvements made around hyper-converged infrastructure (HCI), hybrid capabilities such as Azure File Sync and Azure Site Recovery, our new administrative experience with the Windows Admin Center (WAC), and an array of pretty mind-blowing storage enhancements. In this article, we’ll describe some of the principles that help guide our thinking when designing security solutions and delve into a few of the innovations and enhancements we made to security in this latest Windows Server release.
Security has long been a top priority in Windows Server and that continues with Windows Server 2019. Over the years, we’ve not only invested a huge amount in developing mitigation for well-known attack vectors of the day, but also in trying to better understand how the attacks evolve over time and anything they might share in common.
The table below highlights some of the more notable takeaways from our ongoing work and research.
| 1. | The network is no longer the security perimeter (it hasn’t been for some time) | Identity is the (new) security perimeter |
| 2. | Entry—we can’t stop this from happening | People will be fooled, bribed, blackmailed, etc. |
| 3. | Eliminating human error isn’t possible | Phishing works and will continue to do so |
| 4. | Insider-attacks are a big problem | Anomalous activity monitoring helps in detection; limit access through identity management and isolation |
| 5. | Compliance is very important | But compliance and security are not the same thing: compliant != secure |
| 6. | Prevention methods aren’t always technical or architectural | Many will be operational and that will impose some level of additional operational friction—security has a price $$$ |
At a high-level then, our efforts boil down to 4 core, and mostly self-explanatory guiding principles (on the left) across 3 technology dimensions (on the right). It’s worth calling out that one of those technology dimensions, managing privileged identities, has never been more important than it is today given that identity and strong authentication is steadily replacing the network as the security perimeter.
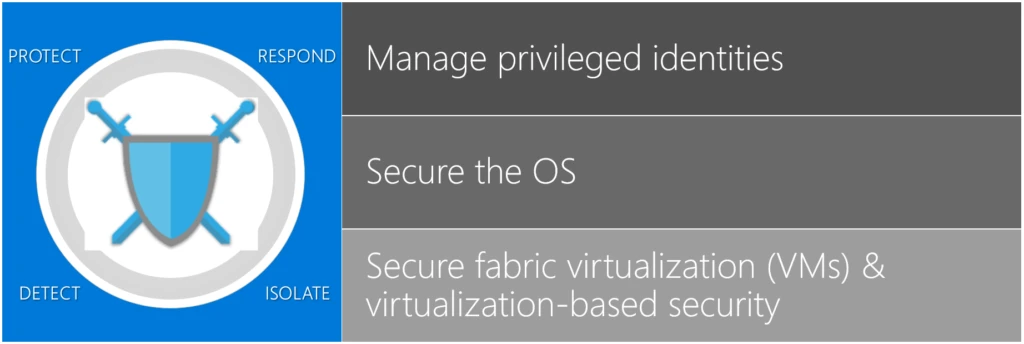
These guiding principles and areas of focus help us ensure that we not only provide reactive mitigation to what are sadly becoming commonplace threats, but that we also build in proactive measures that prevent attacks from ever starting in the first place. Stated succinctly, security isn’t a bolt-on, it’s an architectural principle and one that both Windows 10 and Windows Server 2019 are walking (well, running if you’ll excuse the pun) incarnations of. That’s enough of our mental model, let’s get on with discussing some of the new capabilities in Windows Server 2019.
The privileged identity management capabilities provided by Windows Server 2016, such as Just Enough Administration (JEA) and Credential Guard carry forward into Windows Server 2019. For the purposes of this blog then, we’ll focus on a few of the other technologies that embrace the latter two dimensions: securing the OS and providing secure fabric virtualization and virtualization-based security (VBS).
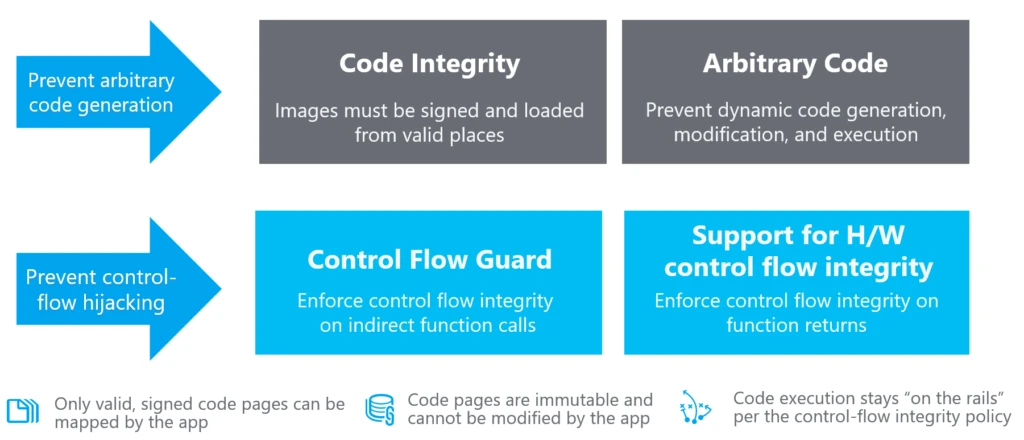
This example takes us well-down into the weeds of just two of the ways that the OS protects itself by ensuring that only legitimate, whitelisted code can run and that, when it does, it runs in the manner it was intended to.
With Windows Defender Application Control (WDAC), administrators can create policies that block anything from running unless it’s included in the whitelisted policy. Because the WDAC policy is enforced by the hypervisor, its control extends even to kernel mode components like drivers.
Note that we mentioned that the policy is enforced by the hypervisor, not Hyper-V. It’s pretty easy to conflate hypervisor and Hyper-V as one and the same thing—they’re actually not the same thing. At its core, a hypervisor controls the hardware’s native virtualization capabilities and Windows uses it in two distinct ways:
With WDAC in Windows Server 2019, you can now “stack” multiple policies on top of one another to create a whitelist that is the aggregate of all stacked policies. It’s even possible to create a policy that allows the WDAC policy to be changed without requiring a reboot!
Control Flow Guard (CFG) provides built-in platform security designed to combat intentional memory corruption vulnerabilities by placing restrictions on where an application can execute code from thereby making it much harder for malicious software to execute arbitrary code through vulnerabilities such as buffer overflows. With Windows Server 2019, we’ve added support for kernel-mode CFG, too.
With Windows Server 2019, you’re now able to protect your Linux workloads by running them inside shielded VMs. By leveraging the same protections as Windows VMs including Secure Boot, template disk signing, a secure provisioning process, and TPM-sealed disk encryption keys, you’re able to protect data in your Linux VMs at rest and in flight when migrating the VM between two Hyper-V hosts. Under the hood, we’re leveraging the native dm-crypt disk encryption technology to enable the VM to encrypt itself and ensure the VM owner is the only entity with access to the disk encryption passphrases. Learn how to get started with Linux shielded VMs and check out the open source tools that power them.
In Windows Server 2019, we are introducing a new attestation mode based on asymmetric key pairs called Host Key attestation. This mode is designed to greatly simplify setup in environments where TPM attestation is not possible. It offers similar assurances to the existing Active Directory attestation mode, in that possession of the key is enough to be able to run shielded VMs, but does not require an Active Directory trust to be established (the hosts don’t even need to be domain joined). A TPM is not required on the Hyper-V host, which also means that HGS will not validate the hardware or software configuration on the host as it does with TPM mode. Check out how to deploy the Host Guardian Service and configure it and Hyper-V hosts for Host Key attestation.
There’s a huge array of new capabilities in Windows Server 2019 so it’s well worthwhile getting yourself ahead of the learning curve by downloading the Windows Server 2019 preview release and giving these new capabilities a test drive yourself. You can also join the conversation going on in the Windows Server Tech Community space.
Check out the previous blog posts in this series: