In this blogpost, we will show you how to provision a Jenkins virtual machine and setup a CI/CD pipeline to build an ASP.NET Core application stored in GitHub and deploy the application into Azure Kubernetes Service (AKS).
We start from the solution template in Azure Marketplace since that’s the fastest and easiest path to get Jenkins up and running in Azure. You can follow the steps using your existing Jenkins server, regardless of whether it’s run on premises or in the cloud. The deployment target is Azure Kubernetes Service. It manages your hosted Kubernetes environment, making it quick and easy to deploy and manage containerized applications without container orchestration expertise. It also eliminates the burden of ongoing operations and maintenance by provisioning, upgrading, and scaling resources on demand, without taking your applications offline.
This is the flow implemented in this post:
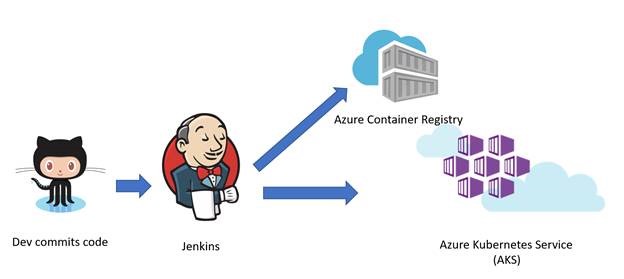
- Developers commit code change into GitHub
- Jenkins builds the application into a Docker image
- Jenkins pushes the Docker image into Azure Container Registry
- Jenkins deploys the Docker image into Azure Kubernetes Service
Prerequisites
Deploy Jenkins server
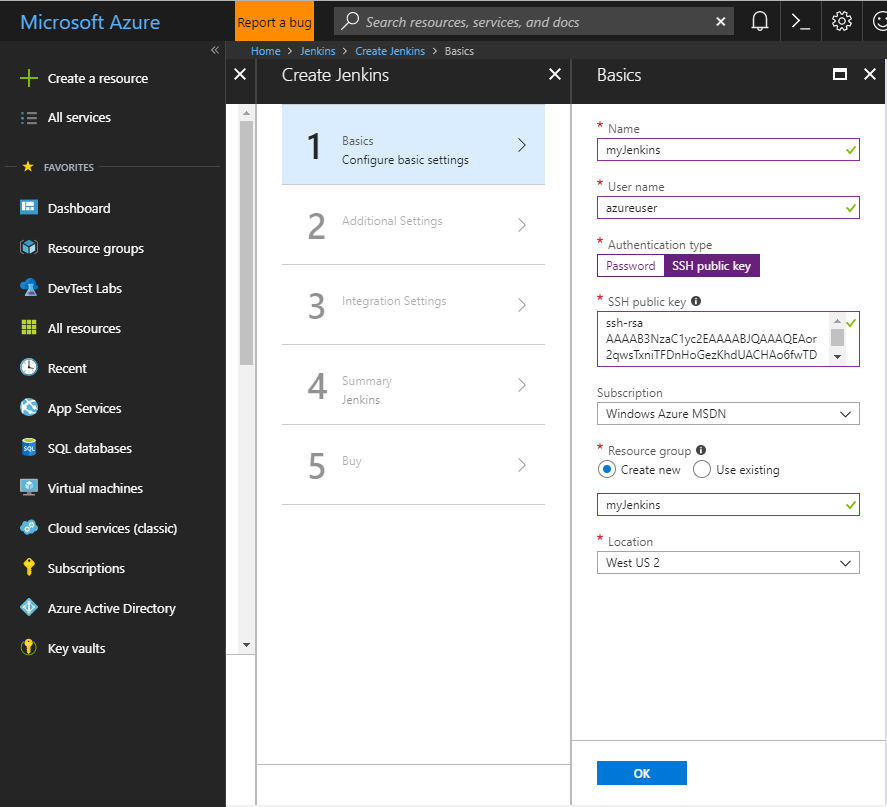
In the Azure portal, select Create a resource and search for Jenkins. Select the Jenkins offering with a publisher of Microsoft and select Create.
Enter the following information on the basics form and click OK when done.
- Name – name for the Jenkins deployment.
- User name – this user name is used as the admin user for the Jenkins virtual machine.
- Authentication type – SSH public key is recommended. If selected, copy in an SSH public key to be used when logging into the Jenkins virtual machine.
- Subscription – select an Azure subscription.
- Resource group – create a new or select an existing resource group.
- Location – select a location for the Jenkins server.
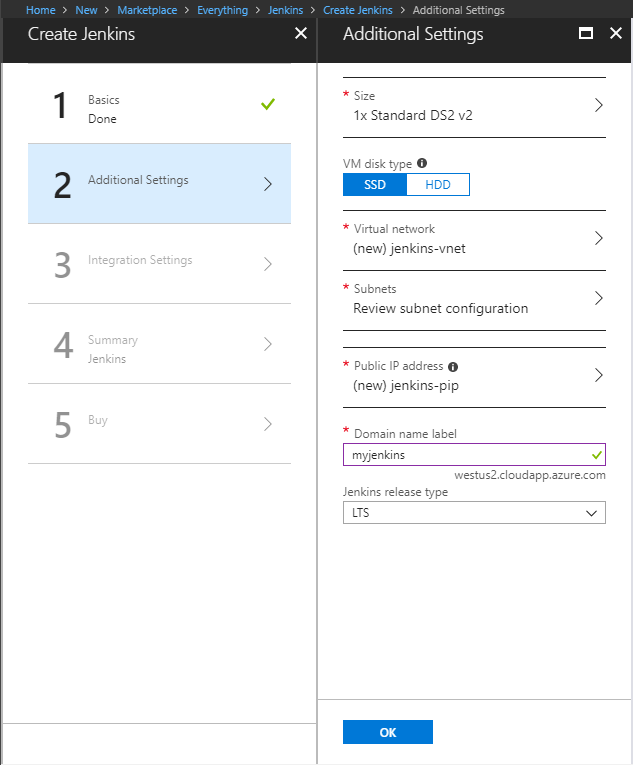
On the additional settings form, complete the following items:
- Size – Select the appropriate sizing option for your Jenkins virtual machine.
- VM disk type – Specify either HDD (hard-disk drive) or SSD (solid-state drive) for the Jenkins server.
- Virtual network – (Optional) Select Virtual network to modify the default settings.
- Subnets – Select Subnets, verify the information, and select OK.
- Public IP address – Selecting the Public IP address allows you to give it a custom name, configure SKU, and assignment method.
- Domain name label – Specify a value to create a fully qualified URL to the Jenkins virtual machine.
- Jenkins release type – Select the desired release type from the options: LTS, Weekly build, or Azure Verified.
For Integration Settings, select No to use Jenkins host to build the jobs.
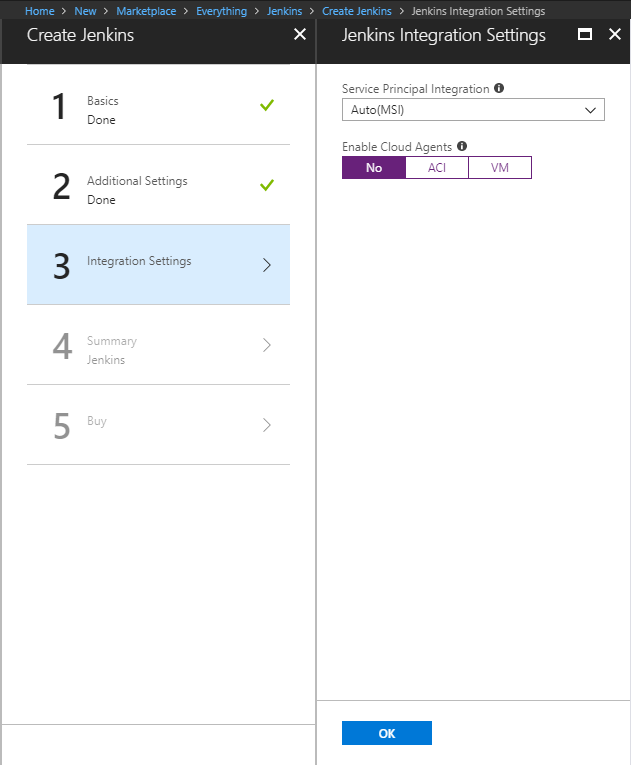
If you want to use ACI or VM build agent, you can refer https://docs.microsoft.com/en-us/azure/container-instances/container-instances-jenkins & https://wiki.jenkins.io/display/JENKINS/Azure+VM+Agents+plugin
Once done with the integration settings, click OK, and then OK again on the validation summary. Click Create on the Terms of use summary. The Jenkins server takes a few minutes to deploy.
Configure Jenkins
Get initial admin password
In the Azure portal, browse to the Jenkins Resource Group, select the Jenkins virtual machine, and take note of the DNS name.
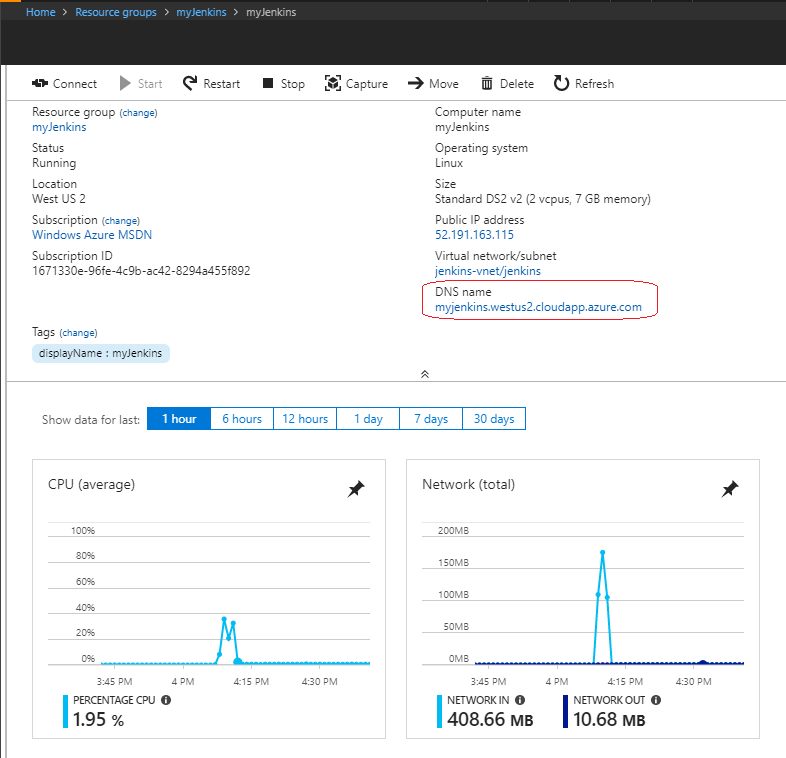
Browser to the DNS name of the Jenkins VM and copy the returned SSH string.
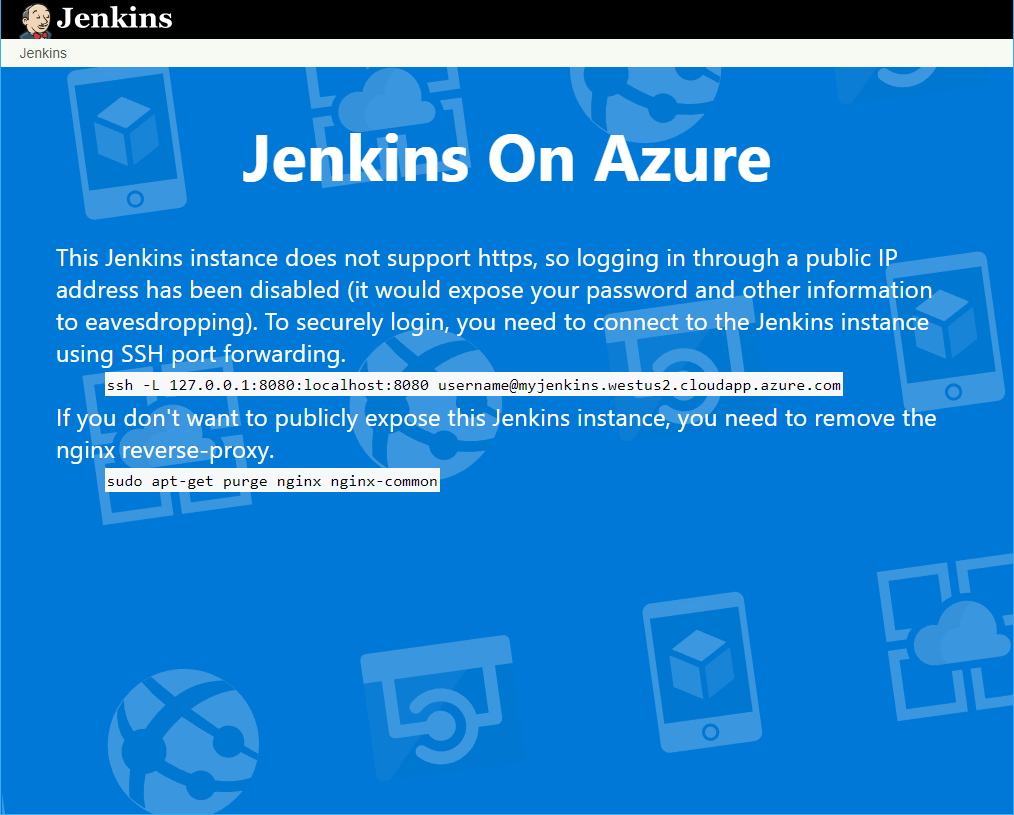
Open up a terminal session on your development system, and paste in the SSH string from the last step. Update ‘username’ to the username specified when deploying the Jenkins server.
Once connected, run the following command to retrieve the initial admin password.
sudo cat /var/lib/jenkins/secrets/initialAdminPassword
Deploy secrets into Azure AKS
- Install Azure CLI
- Install Docker
- Install kubectl
- Get AKS credentials
az aks get-credentials --resource-group ${resource_group} --name ${aks_name} --admin
- Deploy secret of Azure ACR
(You can skip this step if you have already done it in first-time deployment)
kubectl create secret docker-registry regsecret --docker-server=${acr_server} --docker-username=${acr_username} --docker-password=${acr_password} --docker-email=${your_email}
- Deploy secret of Application Insights instrumentation key
(You can skip this step if you have already done it in first-time deployment)
kubectl create secret generic aspnetcoredemo-secrets --from-literal=AppInsightsKey=${ai_key}
- Copy AKS credential to Jenkins folder
sudo mkdir /var/lib/jenkins/.kube
sudo cp .kube/config /var/lib/jenkins/.kube/
sudo chmod 777 /var/lib/jenkins/.kube/config
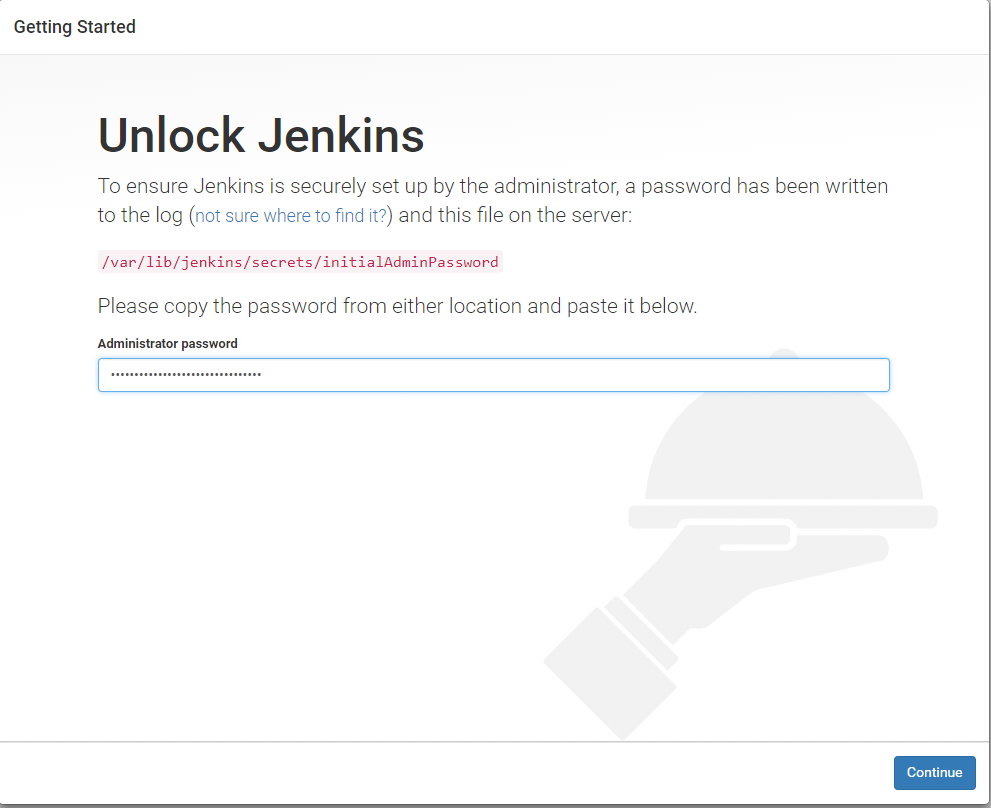
Leave the SSH session and tunnel running, and navigate to http://localhost:8080 in a browser. Paste the initial admin password into the field as seen in the following image. Select Continue when done.
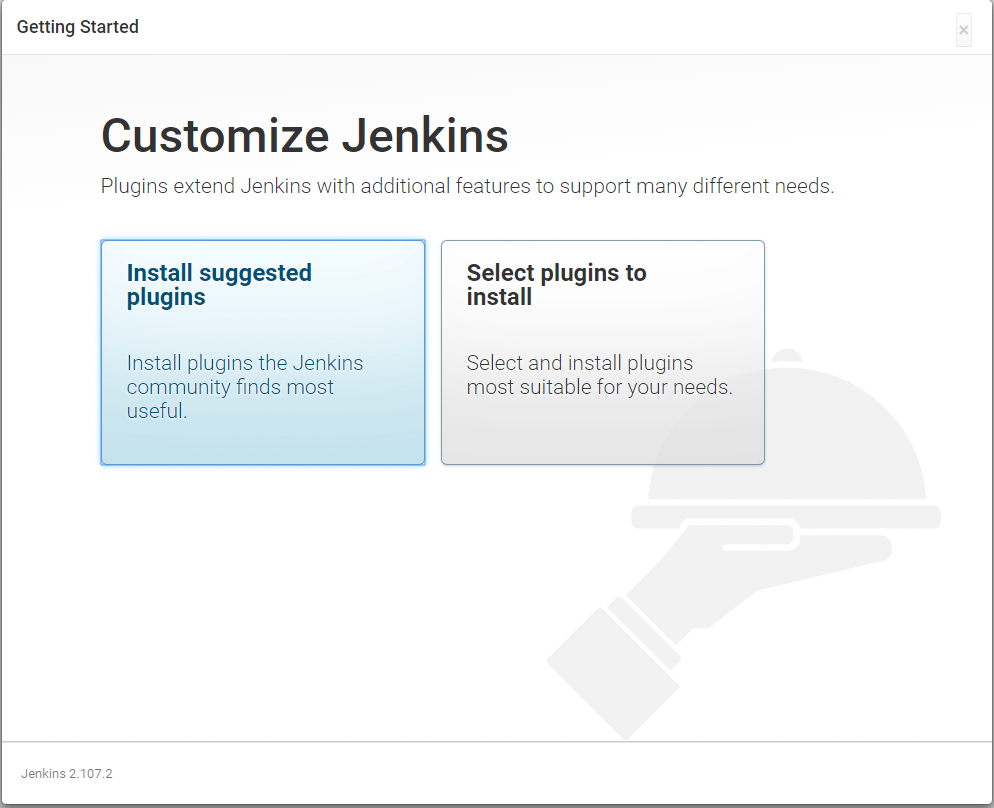
Select Install suggested plugins to install all recommended Jenkins plugins.
Create a new admin user account. This account is used for logging into and working with your Jenkins instance.
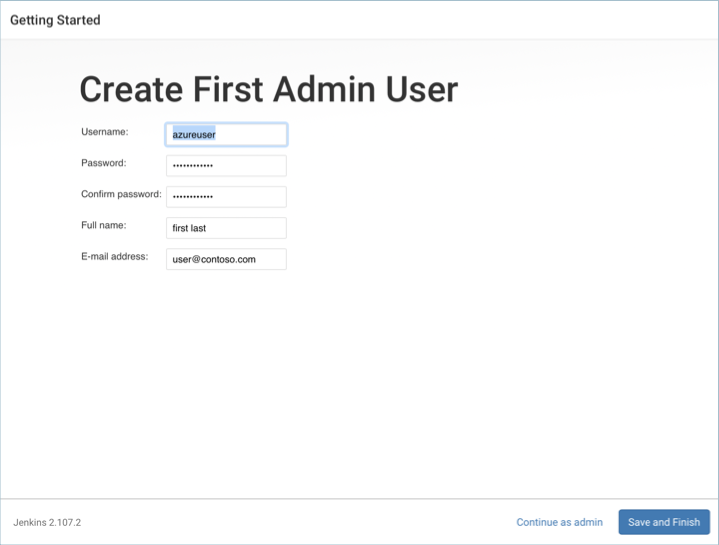
Select Save and Finish when done, and then Start using Jenkins to complete the configuration.
Jenkins is now configured and ready to build and deploy code. For this example, a simple asp.net core application is used to demonstrate a Jenkins build. It can be found at https://github.com/mjrousos/AspNetCore-Sample.
Create Pipeline build job and deploy to Azure AKS
Now create a Jenkins build job. Select New Item, give the build project a name such as aspnetcore-webapp, select Pipeline, and click OK.
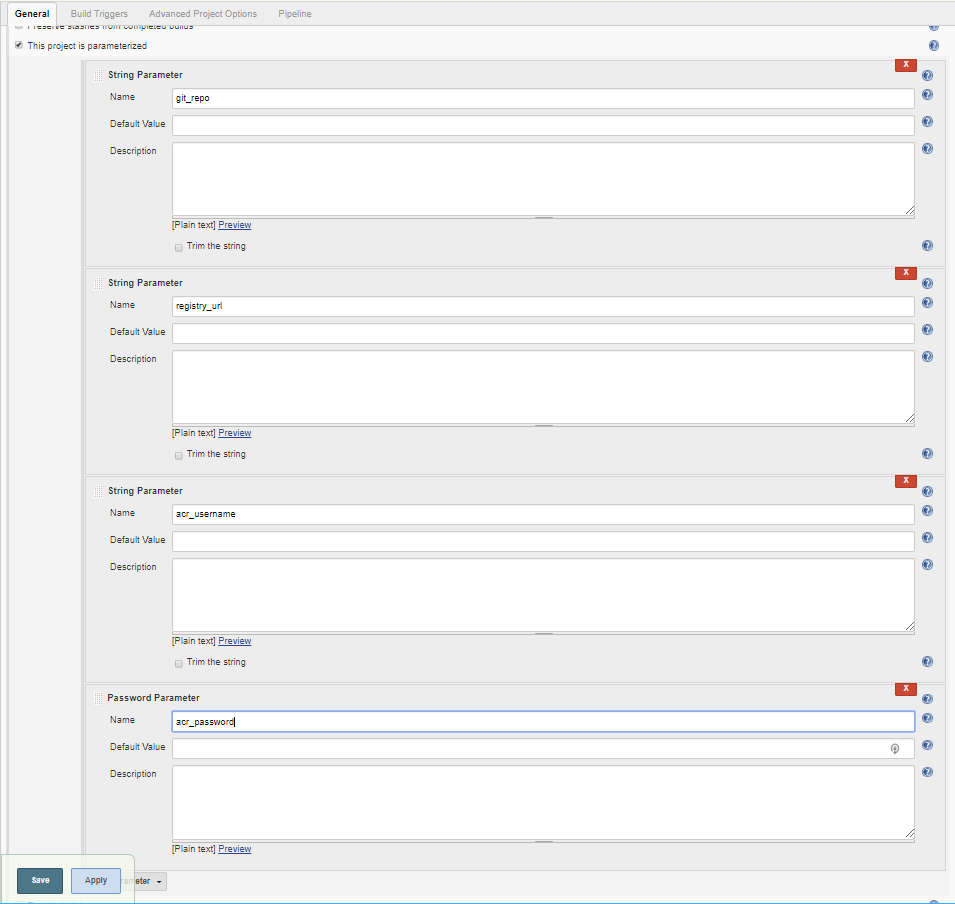
Define parameters “git_repo”, “acr_username”, “acr_password”, “registry_url”.
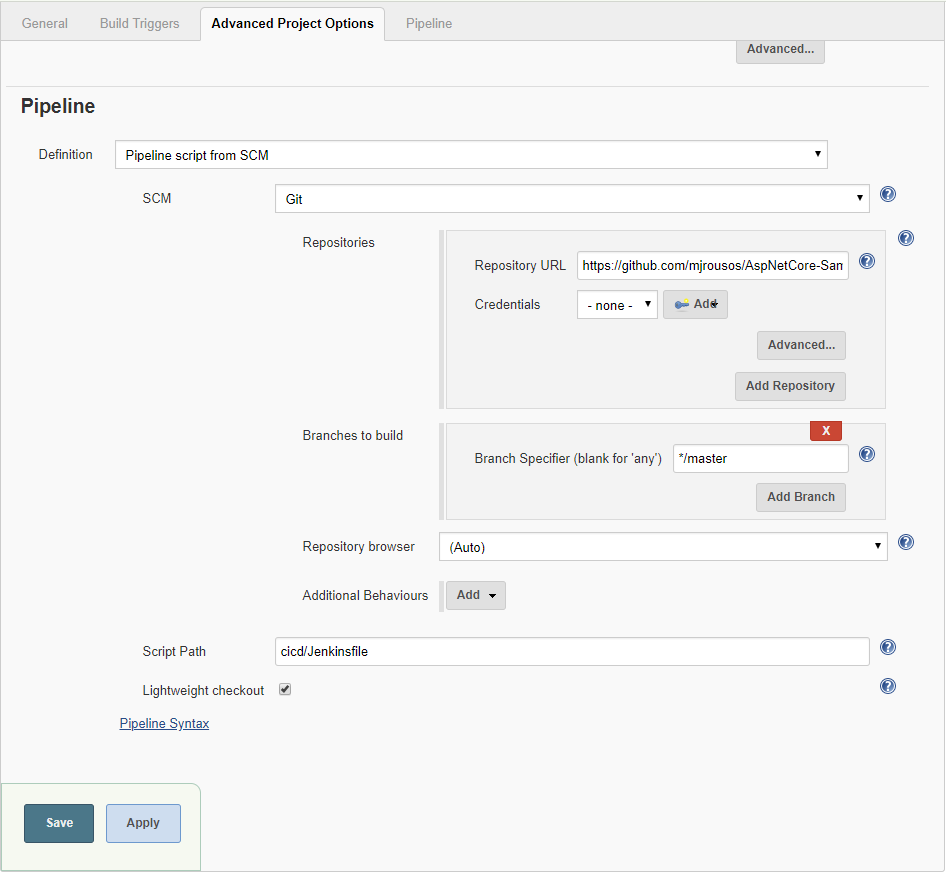
Under Pipeline, set Definition to Pipeline script from SCM, Repository URL to https://github.com/mjrousos/AspNetCore-Sample.git and Script Path to cicd/Jenkinsfile.
Run the build job
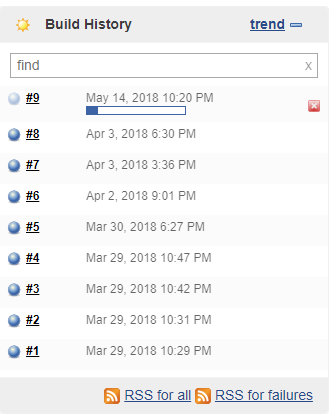
To test the build job, manually start a build.
Select Build Now to start a build job. It takes a few seconds for the job to start, when running, you should see status similar to the following images.
Here you go…
Questions or feedback? Let us know in the comments below.
